ClickFix Scams: The Social Engineering Threat Targeting Small Businesses in 2025
Complete guide to ClickFix attacks targeting small businesses. Learn how this social engineering technique works, why attacks increased 517% in 2025, and how to protect your organization.

Key Takeaway
ClickFix attacks have increased 517% in 2025, representing 8% of all blocked cyberattacks. This social engineering technique tricks users into executing malicious commands by copying and pasting seemingly legitimate "fixes" for technical issues. Small businesses face heightened risk as these attacks bypass traditional security measures and exploit human trust.
Security researchers have documented a notable increase in ClickFix attacks throughout 2025. This social engineering technique manipulates users into running malicious commands on their own computers and has become increasingly common in the threat landscape, warranting attention from business owners and IT professionals.
Understanding the ClickFix Phenomenon
ClickFix represents a fundamental change in social engineering tactics. Unlike traditional malware that requires sophisticated technical exploits, these attacks succeed by exploiting something far more predictable: human behavior and our natural inclination to resolve technical problems.
The attack methodology is relatively straightforward. Users encounter what appears to be a legitimate error message or security notification on a website. The message claims that an issue with their browser, camera access, or system security requires immediate attention. To "fix" the problem, users are instructed to copy a provided command and paste it into their computer's Run dialog box or PowerShell terminal.
Users may not realize that this command is a malicious script designed to download and install malware on their system. According to recent ESET research, the technique has proven effective enough to become the second most common attack vector behind traditional phishing.
The 2025 Surge: Current Statistics
Recent data reveals the concerning growth of ClickFix attacks throughout 2025:
2025 ClickFix Attack Statistics
- 517% increase in ClickFix attacks during the first half of 2025
- 8% of all blocked attacks now utilize ClickFix techniques
- 400% growth in phishing URLs tied to ClickFix between May 2024 and May 2025
- 10% increase in drive-by compromises attributed to ClickFix campaigns
These statistics reflect the growing adoption of ClickFix techniques. The success rate of ClickFix attacks has attracted both opportunistic criminals and sophisticated state-sponsored groups from North Korea, Iran, and Russia.
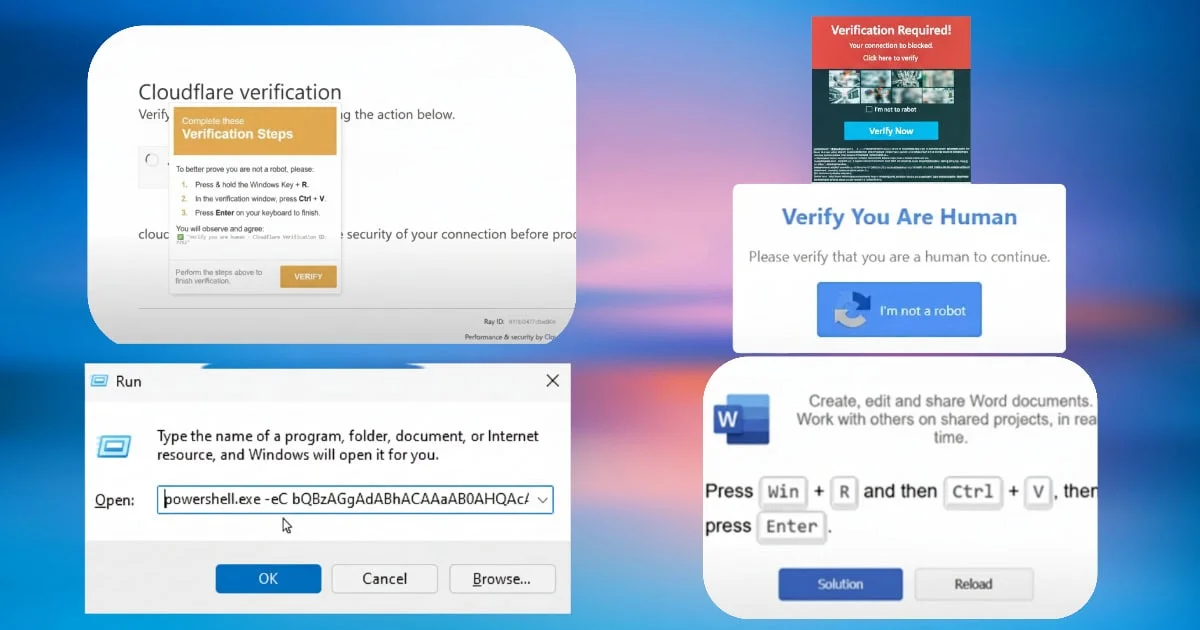
How ClickFix Attacks Unfold
The typical ClickFix attack follows a predictable but effective pattern:
Initial Contact
Attackers begin by compromising legitimate websites or creating convincing replicas of popular services. Recent campaigns have targeted streaming sites, fake Google Meet pages, and even impersonated government services like the U.S. Social Security Administration.
The Deception
Users encounter a pop-up or error message claiming a technical issue requires immediate action. Common scenarios include:
Common ClickFix Scenarios
- Fake browser update requirements
- CAPTCHA verification requests
- Camera or microphone access problems
- Security verification checks
- Document display errors
The Social Engineering Hook
The attack exploits several psychological triggers:
- Urgency: Messages suggest immediate action is required
- Authority: Official-looking branding and terminology
- Helpfulness: Providing a "simple solution" to a technical problem
- Trust: Using familiar interfaces and well-known brand aesthetics
The Execution
Users are presented with step-by-step instructions to "resolve" the issue:
- Press Windows + R to open the Run dialog
- Copy the provided "fix" command
- Paste it into the Run box
- Press Enter to execute
Users may not realize they've just granted attackers access to their system.
Recent Evolution and Targeting
The ClickFix landscape has developed throughout 2025, with several notable developments:
State-Sponsored Adoption
Nation-state actors have begun incorporating ClickFix into their arsenals. Notable examples include:
State-Sponsored ClickFix Campaigns
- North Korean groups (TA427/Kimsuky): Targeting think tanks and policy organizations with fake diplomatic meeting requests
- Iranian actors (TA450/MuddyWater): Using the technique to deploy remote monitoring tools
- Russian groups (TA422/APT28): Integrating ClickFix into existing espionage campaigns
Industry-Specific Targeting
Recent campaigns have demonstrated increasing sophistication in targeting specific sectors:
- Healthcare: Malicious code injected into medical education platforms
- Automotive: Over 100 car dealership websites compromised through third-party streaming services
- Financial Services: Fake payment and invoice notifications targeting accounting departments
- Government: Impersonation of tax authorities and social security systems
Why Small Businesses Are Particularly Vulnerable
Small and medium-sized businesses face unique challenges that make them prime targets for ClickFix attacks:
Small Business Vulnerability Factors
Limited Security Resources
Unlike large enterprises, small businesses often lack dedicated cybersecurity teams and rely on basic security tools that may not detect social engineering attacks.
Mixed IT Environments
Small businesses frequently operate with a combination of personal and business devices, varying levels of security software, and inconsistent update policies.
Trust-Based Operations
Smaller organizations often operate with high levels of interpersonal trust, making employees more likely to help resolve what appears to be a technical problem.
Insufficient Training
Many small businesses lack comprehensive cybersecurity awareness programs, leaving employees unprepared to recognize sophisticated social engineering tactics.
Real-World Impact and Consequences
Successful ClickFix attacks can have serious consequences for small businesses:
Immediate Technical Impact
Technical Consequences
- Installation of information-stealing malware
- Compromise of business credentials and passwords
- Installation of remote access tools allowing persistent attacker presence
- Potential deployment of ransomware
Business Consequences
- Theft of customer data and business intelligence
- Financial losses from compromised banking credentials
- Regulatory compliance violations and potential fines
- Reputational damage and loss of customer trust
- Business disruption and recovery costs
Long-Term Implications
- Use of compromised systems as launching points for attacks on customers and partners
- Potential liability for data breaches affecting third parties
- Increased insurance premiums and difficulty obtaining cyber coverage
Comprehensive Protection Strategies
Defending against ClickFix attacks requires a multi-layered approach that combines technology, processes, and human awareness:
Technical Safeguards
Endpoint Protection
Implement comprehensive endpoint security solutions that can detect and prevent the execution of malicious PowerShell commands. Modern endpoint detection and response (EDR) tools can identify suspicious command patterns even when they're executed by legitimate users.
Email Security
Deploy advanced email filtering solutions that can identify and block ClickFix-related phishing campaigns. Look for solutions that use behavioral analysis and machine learning to detect novel attack patterns.
Web Protection
Utilize DNS filtering and web security gateways to prevent access to known malicious domains hosting ClickFix campaigns. These solutions provide real-time protection against emerging threats and offer comprehensive DNS-layer security for businesses of all sizes.
Process Improvements
Develop and regularly test incident response procedures specifically for social engineering attacks. Ensure employees know how to report suspicious activity and who to contact. Our cybersecurity assessment guide can help you evaluate your current response capabilities.
Human-Centered Defenses
Security Awareness Training
Conduct regular training sessions that specifically cover ClickFix and other social engineering techniques. Training should be:
- Practical and hands-on, showing real examples
- Regularly updated with current threat information
- Tested through simulated phishing exercises
- Tailored to specific job roles and responsibilities
Verification Procedures
Establish clear procedures for verifying unusual requests or technical issues:
- Never execute commands from web pages or emails
- Always verify technical issues through independent channels
- Contact IT support for any unexpected system problems
- Report suspicious messages or pop-ups immediately
Multi-Factor Authentication
Implement multi-factor authentication across all business systems to provide protection even if credentials are compromised. Consider business-grade password managers like 1Password Business, which offers comprehensive credential management for teams.
Assessment and Implementation
Organizations should consider conducting a comprehensive security evaluation to identify vulnerabilities to ClickFix and other social engineering attacks. Our free cybersecurity assessment guide provides a starting point for understanding your current security posture.
For businesses looking to implement a comprehensive security strategy, consider reviewing our small business cybersecurity guide, which covers essential tools and practices for protecting against modern threats.
Key Consideration
The increase in ClickFix attacks in 2025 reflects ongoing changes in the cybersecurity landscape. Organizations implementing comprehensive cybersecurity awareness and technical protections are better positioned to defend against ClickFix and other social engineering threats.
Frequently Asked Questions
What exactly is a ClickFix attack?
A ClickFix attack is a social engineering technique where cybercriminals trick users into copying and pasting malicious commands into their computer's terminal or Run dialog. The attack displays fake error messages or verification prompts that claim to require user action to "fix" a technical issue.
How can I tell if I'm being targeted by a ClickFix scam?
Common signs include unexpected error messages asking you to copy and paste commands, fake CAPTCHA verification that requires command execution, urgent security warnings with step-by-step "fix" instructions, and prompts to open PowerShell or the Windows Run dialog from websites or emails.
What should I do if I think I've fallen for a ClickFix attack?
Immediately disconnect from the internet, contact your IT support team or a cybersecurity professional, run a comprehensive antivirus scan, change all passwords using a clean device, and monitor financial accounts for unauthorized activity.
Are small businesses really more vulnerable to these attacks?
Yes, small businesses often lack dedicated cybersecurity teams, comprehensive security training programs, and advanced threat detection tools. They also typically operate with higher levels of trust and may use a mix of personal and business devices with varying security levels.
What's the best defense against ClickFix attacks?
The most effective defense combines employee training to recognize social engineering tactics, technical controls like advanced endpoint protection and email filtering, strict policies against executing commands from untrusted sources, and regular security assessments to identify vulnerabilities.
Related Resources
- Best Cybersecurity Software for Small Business – Tool recommendations
- Best Business Password Managers – Credential security
- Small Business Security Assessment Guide – Free assessment tools
- Small Business Breach Prevention Guide – 90-day security plan
- Small Business Cybersecurity Upgrade Guide – Miami IT services
- VPN vs Zero Trust Guide – Access security
- Cybersecurity Services – Professional support
Related Articles
More from Cybersecurity

AI-Powered Cyberattacks: Small Business Defense Guide
Practical guide to defending against AI-enhanced cybersecurity threats. Learn how AI changes common attack methods and build effective protection for $182-308/month with a straightforward 90-day implementation timeline.
18 min read

DMARC for Small Business: 2026 Google & Microsoft Requirements Guide
Complete DMARC implementation guide for 2026 Google, Yahoo, and Microsoft email requirements. Learn SPF, DKIM setup, policy phases, and PCI DSS v4.0 compliance to prevent email spoofing and ensure deliverability.
14 min read

Malwarebytes Business Review 2026: Teams vs ThreatDown Comparison
In-depth review of Malwarebytes Teams and ThreatDown for business security. Pricing, features, testing results, and recommendations for small to medium businesses.
16 min read
