Imagine a world where running multiple cables for all your network devices is a thing of the past. A world where setting up security cameras, wireless access points, and even lighting systems becomes incredibly simple. That's the world of Power over Ethernet (PoE). PoE technology revolutionizes network setups by delivering power and data over a […]
In today's fast-paced business world, digital transformation is not just a buzzword but a critical strategy for survival and success. Yet, for many small to medium-sized business owners, the concept can seem overwhelming, fraught with technical jargon and complex technologies. At IFeelTech, we believe in demystifying tech and making it work for you, not against […]
Key Takeaway: A well-designed server room foundation combining the latest networking technologies—including WiFi 7 access points, Cat6 cabling, and fiber internet connectivity—enables small businesses to build scalable, secure, and future-ready IT infrastructure that supports growth through 2030 and beyond. A strong digital foundation empowers organizations to streamline operations, increase efficiency, and provide exceptional customer experiences. […]
Over the years, we've installed countless UniFi systems for homes and businesses. From our early days of setting up simple networks to deploying complex, multi-access point installations, the UniFi range grew and evolved. The jump from WiFi 5 to WiFi 6 was significant, offering smoother and more reliable installations. But now, as we embrace the […]
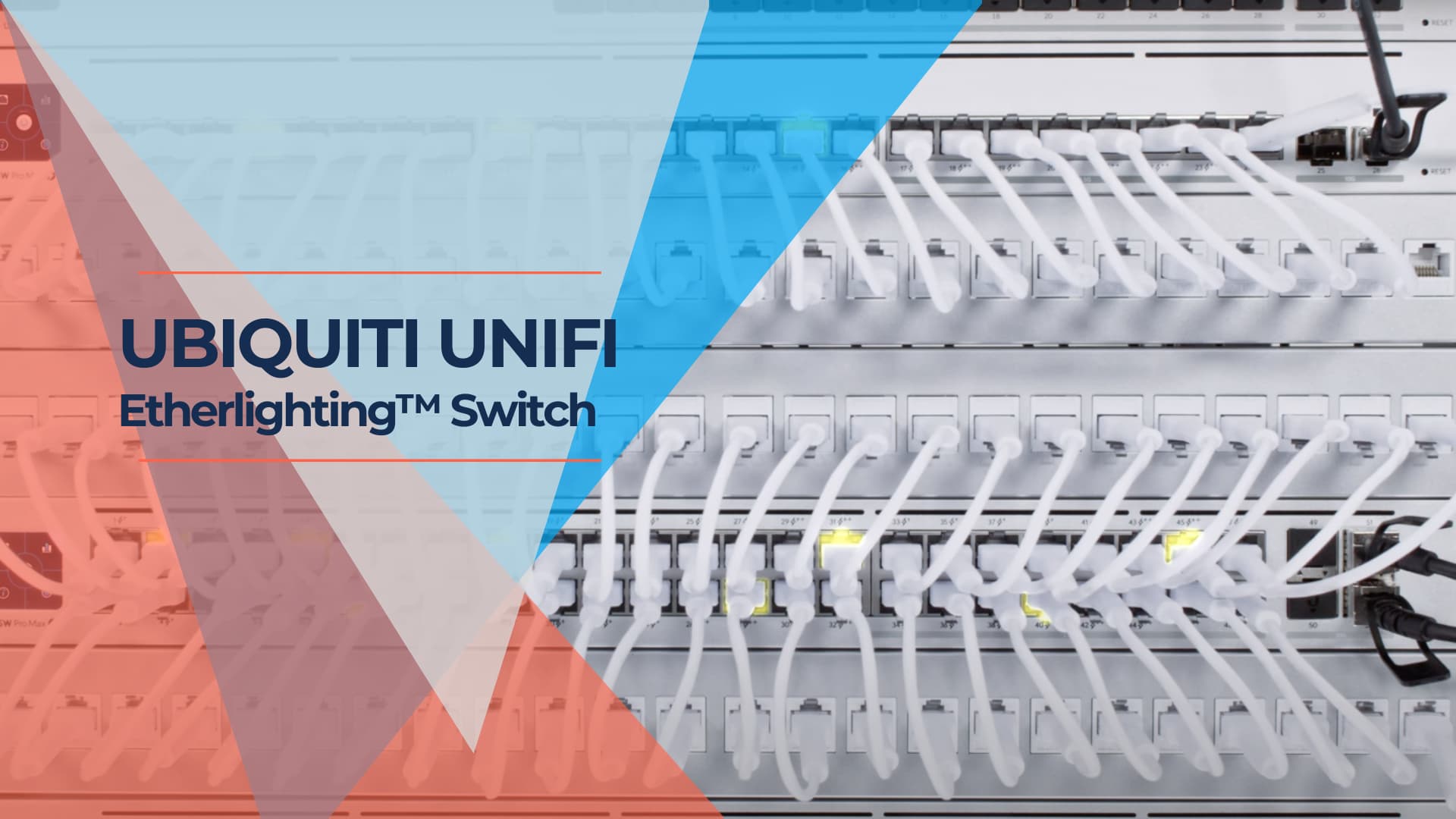
Oh wow, I know very few people out there get excited about something as ostensibly boring as a network switch, but come on, this is so cool! The UniFi Pro Max Switches with Etherlighting™ by Ubiquiti are not just another set of network switches. They're a game-changer in networking technology, blending high-speed data transmission with […]
At iFeeltech, we have firsthand experience with the frustration and confusion caused by these deceptions. Although an age-old trick, invoice fraud continues to evolve, catching even the vigilant guard. Recently, we faced a situation that brought this issue close to home. An “invoice” appeared to come from our company, charging for services never provided. The […]
Looking for a networking solution that won't let you down? Our team of experts understands the importance of having a reliable and efficient platform. Let us help you take your networking game to the next level. After years of experience working with both PFSense and UniFi Dream Machine, we have found that the UniFi Dream […]
Published: December 2023 | Last updated: September 2025 Key Takeaway: Building a reliable business network in 2025 requires understanding three critical components: strategic networking solutions that support AI and cloud workloads, proper network wiring infrastructure that can handle multi-gigabit speeds, and comprehensive support strategies that keep your operations running smoothly. This guide provides the practical […]
In 2024, the cybersecurity landscape for small businesses will be transformed from a mere precaution to an indispensable part of business strategy. This shift is fueled by an increasingly complex digital ecosystem, where threats evolve rapidly, becoming more sophisticated each day. Small businesses have high stakes – a single breach can have catastrophic consequences. It's not […]
In security solutions, Ubiquiti's Unifi Security Cameras emerged as a beacon of innovation in 2023. The need for robust security measures has never been more paramount as the world becomes increasingly interconnected. Once a luxury, security cameras have become a necessity for homes and businesses. But not all cameras are created equal. Enter Ubiquiti's Unifi […]
In the bustling heart of Miami, where businesses thrive and competition is intense, having an edge can make all the difference. One such edge is efficient networking. As an experienced IT company specializing in professional network installation services in Miami, We've seen firsthand how a robust network can propel a business to success. Let me […]
Imagine starting your workday to find unauthorized transactions or discovering confidential business data leaked online. In an era where businesses increasingly rely on digital platforms, ensuring the security of online accounts is not just about safeguarding assets but also about preserving the company's reputation and trustworthiness. Definition of Hacked Accounts A hacked account in the […]
Last Updated: October 2025 | Reading Time: 12 minutes Quick Answer: Windows 11 Home ($139) covers most personal computing needs with core security and productivity features. Windows 11 Pro ($199) adds business-grade capabilities, including domain joining, BitLocker encryption, Remote Desktop hosting, and Group Policy management. With Windows 10 support ending on October 14, 2025, understanding […]
In the late 1970s, the world was introduced to a revolutionary technology: Ethernet. It began as a simple concept for connecting computers over a shared network and has evolved into the backbone of virtually all networking around the world. Today, Ethernet cables are a ubiquitous part of our connected lives, enabling the fast and reliable […]
Introduction to Synology DS923+ NAS In the modern business landscape, data is more than just a collection of numbers and text—it is the lifeblood of an organization. A reliable, secure, and efficient storage solution becomes paramount as businesses generate a lot of data. Enter the Synology DS923+ NAS—a powerhouse designed to meet the rigorous demands […]
Robust network cabling is important in the digital age, where connectivity serves as the backbone of modern businesses. Whether it's a bustling startup or a well-established multinational corporation, the right network cabling ensures seamless communication, data transfer, and overall efficiency. But with an array of options like Cat5, Cat6, Cat7, Cat8, and even Fiber Optic […]
In the fast-paced digital world of 2023, the lifeline of every small business lies in its ability to communicate effectively and securely. Whether connecting with customers, collaborating with team members, or reaching out to suppliers, communication is the glue that binds all aspects of a business. Among the myriad communication tools available, email stands out […]
Ubiquiti Networks has established itself as a leader in cutting-edge networking solutions, delivering enterprise-grade performance at consumer-level pricing. The UniFi line of wireless access points (APs) consistently tops the charts for value, with models like the UniFi U6 series pushing boundaries even further. The UniFi U6 family of access points leverages the latest Wi-Fi 6 […]
Today's businesses rely on their networks for everything from day-to-day communication to critical business operations. When network issues strike, the consequences are real: decreased productivity, missed opportunities, and even damage to your reputation. Network problems are becoming increasingly tricky to diagnose and resolve. The rise of cloud services, remote work, and connected devices all add […]
Technology has become the backbone of businesses across all industries. From startups to multinational corporations, the need for efficient and effective IT solutions is undeniable. This is where IT consulting comes into play. IT consulting, a rapidly growing sector within the consulting industry, provides businesses with technology solutions that solve their immediate IT problems and […]