Running a small business (SMB) means you're likely juggling a million things at once. From managing finances and serving customers to overseeing operations, your plate is full. So, when the topic of cybersecurity comes up, it might feel like just another complex, potentially expensive item on an already overflowing to-do list. You might even think, “We're too small to be a target.”
It's a common thought, but the reality is a bit different. Cybercriminals often see SMBs as appealing targets precisely because they might have fewer defenses than large corporations. The good news? You don't need a massive budget or a dedicated IT department to improve your security posture significantly. Understanding the basic risks and leveraging helpful guides can make a world of difference.
One such guide is the NIST Cybersecurity Framework (CSF), recently updated to version 2.0. Don't let the name intimidate you; it's designed to be a helpful resource for organizations of all sizes.
In this article, we'll explore why cybersecurity is crucial for your business, break down the common threats in plain English, introduce the NIST CSF 2.0 functions, and show how even basic steps can protect your hard work.
Key Takeaways at a Glance
| Key Concept | What It Means for Your SMB |
|---|---|
| Cybersecurity Isn't Just for Giants | Your business size doesn't make you immune; proactive cyber defense is smart business practice. |
| Understand Real Business Risks | Threats like phishing & ransomware aren't just IT problems—they impact operations, finance, & trust. |
| NIST CSF 2.0 is Your Guide | Think of it as a flexible roadmap (not rigid rules) to help organize and improve your security efforts. |
| Think in Cycles (G-I-P-D-R-R) | The 6 CSF Functions provide a logical flow for managing security: Strategy → Preparation → Defense → Detection → Action → Recovery. |
| Simple Steps, Big Impact | Focus on high-value basics: strong authentication (MFA), reliable backups, staff awareness, & updates. |
| Security Builds Business Value | Good practices protect you, build customer trust, and can help meet partner or insurance requirements. |
“Why Bother?” – The Real Risks SMBs Face Today
It's easy to push cybersecurity down the priority list, but understanding the potential impact can shift perspective. It's not about fear; it's about managing realistic business risks. A cybersecurity incident can affect your SMB in several tangible ways:
- Operational Disruption: An attack, like ransomware, can bring your operations to a standstill. Imagine being unable to access customer orders, process payments, or even communicate internally for days or weeks.
- Financial Loss: The costs associated with a cyber incident add up quickly. These include expenses for recovery, potential ransom payments (though strongly discouraged), lost revenue during downtime, and possible regulatory fines, depending on the data involved.
- Reputation Damage: Trust is hard-earned. A data breach or significant service disruption can severely damage the trust you've built with your customers and partners. Rebuilding that reputation takes time and effort.
- Data Loss: Losing critical business information – customer records, financial data, employee details, or proprietary information – can be devastating and have long-term consequences.
Common Cyber Threats Explained Simply
So, what do these risks actually look like in practice? Here are a few common threats facing SMBs, explained without the technical jargon:
Phishing
Think of this as a digital con artist. Phishing attacks often come as deceptive emails, text messages, or social media messages designed to look legitimate (like they're from your bank, a supplier, or even a colleague). They aim to trick you or your employees into clicking a malicious link, downloading infected software, or revealing sensitive information like passwords or account numbers.
“Like a fake but convincing caller trying to get your bank details over the phone.”
Ransomware
This is a type of malicious software (malware) that, once inside your system, encrypts your files or locks your entire computer network. The attackers then demand payment (a ransom) in exchange for the decryption key to get your data back. Paying the ransom is risky, as there's no guarantee you'll regain access, and it encourages further attacks.
“Like someone digitally kidnapping your important files and demanding money for their return.”
Data Breaches
A data breach occurs when unauthorized individuals gain access to sensitive, confidential, or protected information. This could include customer names and addresses, credit card details, employee social security numbers, or private business strategies. Breaches can happen through hacking, malware, accidental exposure, or even physical theft of devices.
“Like a digital break-in where thieves steal your valuable customer records or company secrets.”
Introducing the NIST Cybersecurity Framework (CSF) 2.0: Your Guide, Not Your Rulebook
Fortunately, you don't have to figure out how to defend against these threats from scratch. The National Institute of Standards and Technology (NIST), part of the U.S. Department of Commerce, develops standards and guidelines across various industries. Their Cybersecurity Framework (CSF), recently updated to version 2.0, is a valuable resource.
Think of NIST CSF 2.0 as:
- A Voluntary Framework: It's not a law or regulation you must follow (unless required by specific contracts or industry mandates). It's a set of best practices and recommendations.
- A Common Language: It helps structure conversations about cybersecurity risk and actions.
- Scalable: Its principles can be applied by organizations of any size, including SMBs.
- A Guide: It provides a logical approach to managing and reducing cybersecurity risk.
The framework is organized around six core functions. Let's break those down.
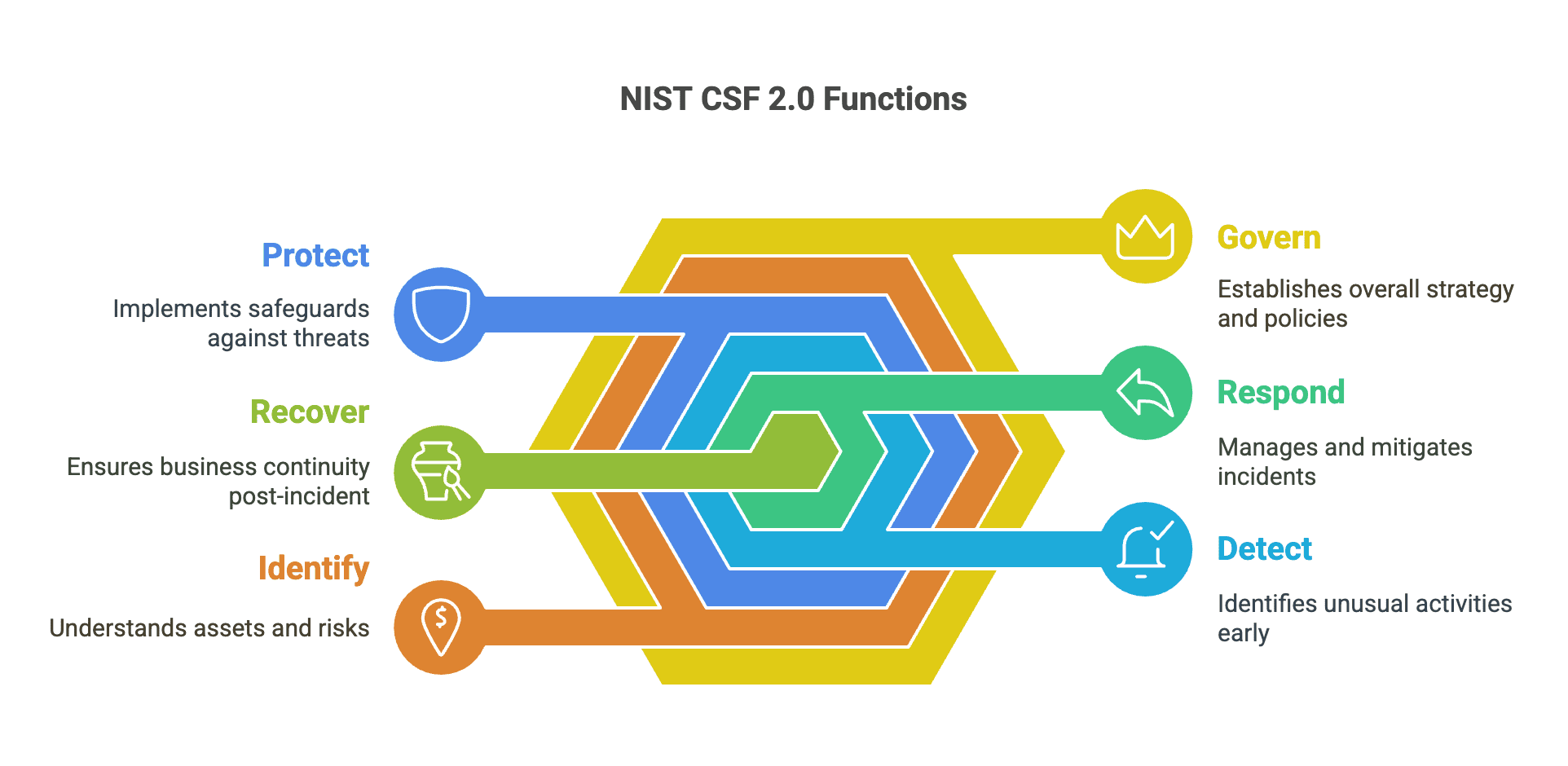
The NIST CSF 2.0 Functions: A Simple Breakdown for Your Business
Instead of technical complexity, think of these functions as logical steps or areas of focus for managing cybersecurity within your business:
Govern: Setting the Strategy
This is about establishing your business's overall cybersecurity risk management strategy, expectations, and policies. Who is responsible for cybersecurity? What are the priorities? How does cybersecurity support your business goals? This function emphasizes that cybersecurity is a leadership and organizational responsibility.
Identify: Knowing What You Have & What Needs Protecting
You can't protect what you don't know you have. This involves understanding your business environment:
- What hardware (computers, servers, phones) do you use?
- What software and systems are critical?
- Where is your important data stored (customer info, financials)?
- What are the potential cybersecurity risks associated with these assets?
Protect: Putting Up Defenses
This function focuses on implementing appropriate safeguards to ensure the delivery of critical services and limit the impact of potential cybersecurity events. Examples include:
- Using strong passwords and multi-factor authentication (MFA)
- Keeping software updated (patching vulnerabilities)
- Training employees on security awareness (like spotting phishing emails)
- Backing up important data regularly
- Controlling who has access to sensitive information
Detect: Spotting Trouble Early
This involves implementing activities to identify the occurrence of a cybersecurity event promptly. How can you tell if something unusual or malicious is happening on your network or devices? This might include:
- Monitoring network traffic for odd patterns
- Reviewing system logs
- Setting up alerts for suspicious login attempts
Respond: Having a Plan for Incidents
Despite best efforts, incidents can happen. This function focuses on having a plan to take action when a cybersecurity event is detected. What are the steps?
- Containing the impact of the incident (e.g., isolating an infected computer)
- Notifying relevant parties (customers, legal counsel, law enforcement if necessary)
- Analyzing the incident to understand what happened
Recover: Getting Back to Business
This function supports timely recovery to normal operations after an incident. The key here is resilience. Activities include:
- Restoring systems and data from backups
- Fixing the vulnerabilities that were exploited
- Communicating with stakeholders during the recovery process
- Updating your response plan based on lessons learned
Scenario: A Local Bakery's Bad Day & How Basic Steps Could Have Helped
Let's revisit the scenario: a local bakery gets a convincing phishing email appearing to be from a supplier. An employee clicks a link, inadvertently downloading ransomware. The bakery's customer order system and point-of-sale terminals are encrypted. They lose access to current orders and customer contact information and can't process sales easily. Chaos ensues.
How could basic steps, aligned with the CSF functions, have made a difference?
- Protect:
- Regular, tested backups of the order system and customer data (Recover also relies on this). They could restore data without paying ransom, minimizing downtime if they had recent backups.
- Basic employee training on identifying phishing emails could have prevented the initial click.
- Up-to-date antivirus software and email filtering might have blocked the malware.
- Identify:
- Recognizing the critical importance of the order and POS systems might have led to prioritizing backups and security for those specific assets.
- Respond/Recover:
- A simple incident response plan (even knowing who to call first – an IT support contact?) could have streamlined the reaction. Having tested backups is the cornerstone of ransomware recovery.
This example shows that cybersecurity isn't about eliminating risk entirely, but significantly reducing its likelihood and impact through practical measures.
The Payoff: Why Basic Cybersecurity Alignment is Good for Business
Investing time and resources (even minimal ones) into basic cybersecurity hygiene isn't just an expense; it's an investment with real returns:
- Reduced Risk: The most obvious benefit – significantly lowering the chances of costly disruptions, data loss, and financial hits.
- Increased Customer Trust: Customers care about data privacy. Demonstrating that you take security seriously can be a competitive advantage and build loyalty.
- Meeting Expectations: Partners, clients, and cyber insurance providers increasingly expect businesses to have basic security measures in place. Proactive steps can help you meet these requirements.
- Peace of Mind: Knowing you've taken sensible, proactive steps to protect your business allows you to focus more confidently on growth and operations.
Getting Started: Simple, Achievable First Steps
Feeling motivated but not sure where to begin? Here are a few high-impact, relatively simple actions you can take:
- Enable Multi-Factor Authentication (MFA): Add an extra layer of security (like a code sent to your phone) to critical accounts like email, banking, and cloud services. This makes it much harder for attackers to gain access even if they steal your password.
- Back Up Your Data Regularly: Identify your critical business data (customer info, financials, operations) and establish a routine for backing it up. Crucially, store backups separately (offline or in a secure cloud location) and test them periodically to ensure you can actually restore them when needed.
- Train Your Team: Awareness is key. Teach employees how to spot phishing emails, the importance of strong passwords, and safe internet browsing habits. Regular reminders help keep security top-of-mind.
- Keep Software Updated: Immediately apply security patches and updates for operating systems (Windows, macOS), web browsers, and other software. These updates often fix known vulnerabilities that attackers exploit.
Conclusion: Protecting Your Business is Within Reach
Cybersecurity might seem daunting, but it's absolutely relevant and manageable for small and medium-sized businesses. It's not about building impenetrable fortresses but about taking sensible, consistent steps to reduce risk and improve resilience.
Understanding common threats and leveraging frameworks like NIST CSF 2.0 can provide a clear roadmap. Remember, even basic actions like using MFA, backing up data, training staff, and updating software make a significant difference. Taking that first step, and then another, puts you firmly on the path to better protecting the business you've worked so hard to build. It's not about fear but bright, proactive business management.
Helpful Resources
For more information and guidance tailored to SMBs, check out these resources:
- CISA (Cybersecurity & Infrastructure Security Agency) – Cybersecurity Resources for Small and Midsize Businesses (SMBs): https://www.cisa.gov/resources-tools/resources/small-and-midsize-businesses
- NIST (National Institute of Standards and Technology) – Cybersecurity Framework (CSF) 2.0: https://www.nist.gov/cyberframework
- SBA (Small Business Administration) – Cybersecurity Resources: https://www.sba.gov/business-guide/manage-your-business/stay-safe-cybersecurity-threats
Disclaimer: This article provides general informational guidance. It does not constitute exhaustive cybersecurity, legal, or technical advice. Consult with qualified professionals for advice specific to your business situation.