End-to-End Encryption Explained: Privacy for All Platforms
Last Updated on December 16, 2024
I have to be honest with you—until recently, I didn’t fully distinguish between the different types of encryption. I assumed encryption was something you used whenever you wanted to secure data, and that was that. However, recent headlines about privacy breaches and cyberattacks forced us to take a closer look at how we handle data security for ourselves and our clients. It became clear that end-to-end encryption (E2EE) wasn’t just a buzzword but an essential tool for safeguarding sensitive information.
For us, it all started with a password manager. We needed a trusted tool—something secure but, most importantly, private. That’s when we settled on Proton Pass, part of the Proton suite of encrypted tools. From there, encryption became a bigger part of the conversation. We began exploring how E2EE could provide stronger protection for passwords, emails, file sharing, and even everyday communication.
This article reflects what we’ve learned: what end-to-end encryption is, why it matters, and how tools like WhatsApp, Signal, and the Proton suite can help you take privacy and security to the next level.
| Key Takeaway | Details |
|---|---|
| What is E2EE? | E2EE encrypts data at every stage, ensuring only the sender and recipient can access it. |
| Popular Tools | Apps like WhatsApp, Signal, and ProtonMail lead the way in making E2EE accessible. |
| Apple & Google Messaging | While iMessage and Google Messages use E2EE, RCS messaging between them may lack encryption. |
| Governments’ New Stance | Governments now encourage E2EE adoption while balancing privacy and anti-cybercrime efforts. |
| Business Benefits | E2EE supports regulatory compliance, builds trust, and reduces risks from data breaches. |
| Future Developments | Quantum-resistant encryption and seamless integration are shaping the future of E2EE. |
Table of Contents
What is End-to-End Encryption?
End-to-end encryption (E2EE) secures digital communication so that only the sender and the intended recipient can read or access the information being shared. Unlike other types of encryption that might protect data only at certain stages, E2EE keeps data encrypted throughout its entire journey—from the sender's device to the recipient's.
Here’s how it works: When sending a message or file, it gets encrypted on your device using a unique cryptographic key. This encrypted data travels across networks and servers in a scrambled format, unreadable to anyone who intercepts it. The recipient’s device holds the matching key to decrypt the data, ensuring only they can access it. Even the service providers facilitating the transmission cannot read the data.
Why Does This Matter?
E2EE is a response to growing privacy concerns. Traditional encryption methods often leave data vulnerable while it’s stored on servers, giving hackers or unauthorized entities a potential entry point. With E2EE, even if someone breaches a server, they can’t access your information without the decryption keys, which only exist on the sender’s and recipient’s devices.
Key Features of E2EE:
- Comprehensive Protection: Data stays secure at every stage—during transmission, on servers, and in storage.
- Limited Access: Only the intended parties can access the data. Not even service providers like WhatsApp or ProtonMail can view it.
- Defense Against Interception: Even if attackers intercept the data in transit, it remains indecipherable without the key.
Example: WhatsApp and the Rise of E2EE
When WhatsApp introduced end-to-end encryption in 2016, it set a new benchmark for secure communication. The platform encrypts all messages, calls, and media using the Signal Protocol. Whether you’re chatting with a friend or sharing sensitive business details, only you and the person you’re communicating with can access the content—no one else, not even WhatsApp.
E2EE is not just a technical solution; it’s a principle of digital privacy. It ensures that users maintain control over their data, making it a critical tool for businesses and individuals navigating an increasingly interconnected world.
Real-Life Examples of E2EE Applications
End-to-end encryption is no longer confined to niche use cases. It’s now integrated into popular tools and platforms used by millions daily, demonstrating its versatility and importance. Let’s explore some standout examples of how E2EE is being used effectively:
1. WhatsApp: Simplifying Privacy for Everyday Use
As one of the world’s most widely used messaging apps, WhatsApp brought E2EE into the mainstream when it adopted the Signal Protocol in 2016. Every message, call, photo, and video shared on WhatsApp is encrypted end-to-end by default.
This means that whether you’re sending a personal message to a friend or discussing sensitive business matters, only you and the recipient can access the content. Even WhatsApp’s parent company, Meta, cannot decrypt these conversations—a feature that has drawn praise and criticism alike.
2. Signal: Privacy for the Privacy-Conscious
Signal has long been a favorite among privacy advocates for its open-source transparency and rigorous encryption standards. Every communication on Signal—whether it’s a text message, voice call, or file transfer—is protected by E2EE.
What sets Signal apart is its commitment to zero data collection. The app doesn’t store metadata, ensuring that even basic details like who you’ve contacted remain private.
3. Proton Suite: Extending Encryption Beyond Messaging
While apps like WhatsApp and Signal focus on communication, the Proton suite takes encryption further, offering a range of tools designed to protect data across multiple use cases. The suite includes:
- ProtonMail for encrypted emails.
- ProtonDrive for secure cloud storage.
- ProtonPass for managing passwords.
Each tool in the Proton suite is built with E2EE at its core, ensuring that sensitive information stays private. ProtonMail, for example, encrypts email content so that even Proton’s servers cannot read your messages.
Apple, Google, and the RCS Gap
Apple and Google both provide end-to-end encryption for their respective messaging platforms—iMessage and Google Messages. However, messages sent between these platforms using RCS (Rich Communication Services) may not be end-to-end encrypted. This inconsistency has raised concerns among privacy advocates and even the FBI, which warns that such gaps could expose users to potential cyber threats. For businesses and individuals alike, this highlights the importance of understanding the encryption capabilities of the tools they rely on.
Governments and Shifting Stances on E2EE
Governments worldwide have long grappled with the balance between privacy and public safety regarding encryption. Initially, many pushed for backdoors in encrypted systems to allow lawful access to data during criminal investigations. However, there has been a notable shift in approach in recent years.
Many governments now recognize the critical role E2EE plays in securing sensitive communications. While encouraging its adoption, they are also crafting sensible laws addressing misuse. For example, initiatives in Europe and parts of Asia emphasize collaboration between technology providers and law enforcement, ensuring that encrypted communication remains private while enabling authorities to combat cybercrime effectively. This evolving stance underscores the growing acceptance of E2EE as a necessary safeguard in the digital age.
Benefits of E2EE for Individuals and Businesses
End-to-end encryption (E2EE) provides a practical and reliable way to enhance privacy and security. Whether used by individuals or businesses, its benefits extend beyond protecting data and fostering trust and compliance in an increasingly connected world.
Benefits for Individuals
- Privacy Protection
- E2EE ensures that personal conversations, documents, and other data stay private. No third party, not even the platform provider, can access the content.
- For instance, messaging on Signal means that only you and the recipient can read your messages, regardless of where they are stored or transmitted.
- Peace of Mind
- Using encrypted services provides reassurance that sensitive information, such as health details or financial discussions, is shielded from unauthorized access.
- Defense Against Cyber Threats
- Encryption mitigates risks from common cyberattacks, such as intercepted communications, by ensuring that data remains scrambled and inaccessible to unauthorized parties.
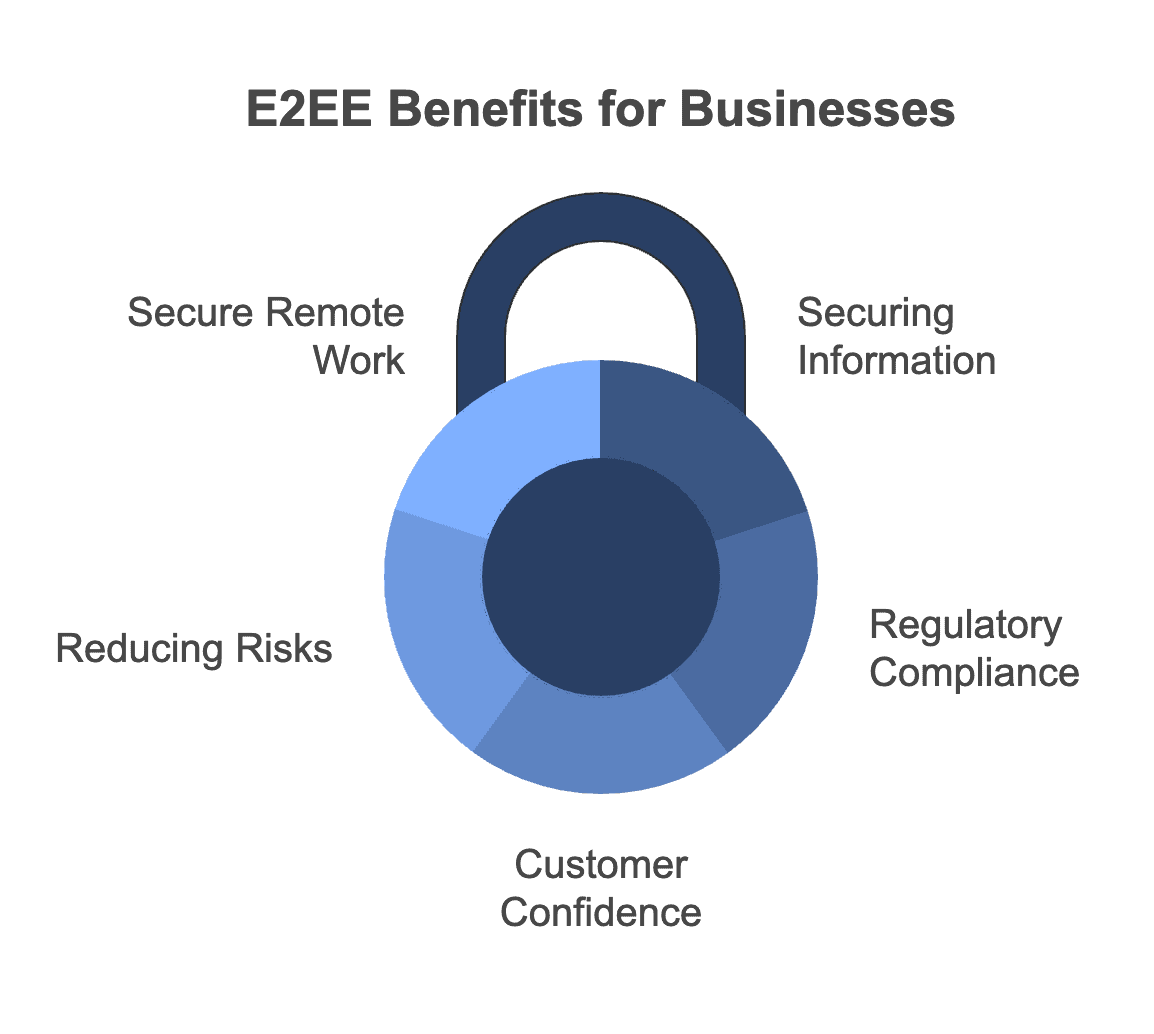
Benefits for Businesses
- Securing Sensitive Information
- Whether it’s client details, intellectual property, or financial records, E2EE ensures critical business data is accessible only to authorized parties. For example, encrypted emails through ProtonMail add an extra layer of protection to legal agreements or financial documents.
- Regulatory Compliance
- Businesses operating in industries with strict privacy laws, such as healthcare or finance, can use E2EE to meet regulatory requirements like GDPR or HIPAA.
- Building Customer Confidence
- By adopting encryption, businesses signal a strong commitment to data security, which can enhance client trust and foster long-term relationships.
- Reducing Internal Risks
- Encrypted data is only accessible with specific keys, minimizing the risk of insider misuse or accidental breaches.
- Supporting Secure Remote Work
- Tools like ProtonDrive enable teams to collaborate securely from anywhere, ensuring that shared files and communications remain private.
Conclusion
End-to-end encryption (E2EE) has emerged as an essential tool for ensuring privacy and security in a digital-first world. From safeguarding personal conversations to protecting sensitive business data, E2EE offers unparalleled assurance that only the intended parties can access shared information. Tools like WhatsApp, Signal, and the Proton suite demonstrate the practical applications of encryption across messaging, email, file sharing, and more.
However, implementing E2EE requires more than just adopting the latest tools. It demands thoughtful integration into workflows, proper key management, and an understanding of its limitations. By addressing challenges such as interoperability and endpoint vulnerabilities, individuals and businesses can maximize the benefits of encryption.
Advancements like quantum-resistant encryption and seamless integration across platforms are set to shape the future of E2EE. Despite debates over lawful access and regulatory concerns, encryption remains a cornerstone of digital privacy, balancing user needs with broader security implications.
At iFeeltech, we’ve seen firsthand how E2EE transforms business data protection. Whether you’re exploring encrypted communication tools or need guidance on integrating E2EE into your operations, we’re here to help. By prioritizing privacy today, you’re building a foundation of trust and security for the future.







Leave a Reply
Want to join the discussion?Feel free to contribute!