Published: June 2025 | Last updated: November 4, 2025
Key Takeaway: Proton Business Suite has established itself as the leading privacy-focused productivity platform, serving over 50,000 organizations worldwide with comprehensive end-to-end encryption across email, calendar, cloud storage, VPN, and password management. Following significant platform updates throughout 2024 and 2025, including achieving SOC 2 Type II certification in July 2025, the suite now represents a mature alternative to mainstream productivity platforms for organizations prioritizing data privacy without compromising essential business functionality.
Proton Business Suite represents a fundamental shift in how organizations approach productivity tools, prioritizing user privacy through comprehensive encryption rather than data monetization. The platform consolidates five essential business services—email, calendar, cloud storage, VPN, and password management—into a single encrypted ecosystem built in accordance with Swiss privacy laws, with a zero-access encryption architecture.
The platform's recent developments include expanding storage allocations from 500 GB to 1 TB per user in August 2024, integrating the Proton Scribe AI writing assistant for enhanced professional communication, and achieving SOC 2 Type II certification in July 2025. These advancements, combined with the existing ISO 27001 certification obtained in May 2024, demonstrate Proton's commitment to meeting enterprise security standards while maintaining its privacy-first approach.
At a Glance
| Rating | 4.2/5 |
| Best For | Privacy-conscious organizations, regulated industries, and remote teams |
| Price | $12.99/user/month (annual billing) |
| Storage | 1 TB per user |
| Key Strength | Comprehensive end-to-end encryption with SOC 2 Type II certification |
| Main Limitation | Limited third-party integrations compared to mainstream platforms |
Strengths
- Comprehensive end-to-end encryption across all services
- SOC 2 Type II and ISO 27001 certified security infrastructure
- Unified platform eliminating multiple vendor relationships
- Swiss privacy law protection and zero-access architecture
- Competitive pricing with included VPN and password management
- Doubled storage capacity (1 TB per user) at no additional cost
Considerations
- Learning curve for teams transitioning from mainstream platforms
- Limited third-party integrations compared to Google Workspace or Microsoft 365
- Performance trade-offs due to encryption overhead
- Fewer advanced collaboration features than enterprise alternatives
Verdict
Proton Business Suite delivers genuine privacy protection without sacrificing essential business functionality, making it an excellent choice for organizations prioritizing data security over convenience features. The combination of comprehensive encryption, recent certifications, and unified platform design creates compelling value for privacy-conscious businesses.
Platform Overview
Proton Business Suite consolidates five essential business services under a single encrypted ecosystem. Unlike traditional productivity platforms that provide encryption as an optional feature, Proton implements zero-access encryption by default, ensuring that even Proton cannot access user data. This approach addresses increasing regulatory requirements and growing awareness of data privacy risks in business environments, particularly as outlined in comprehensive small business security compliance frameworks.
Core Service Components
Proton Mail for Business
The email service provides 20 addresses per user and supports 15 custom domains. It features the Proton Scribe AI writing assistant for enhanced professional communication. IMAP/SMTP support ensures compatibility with existing email clients while maintaining end-to-end encryption for all messages. Advanced filtering, password-protected emails, and encrypted contact details provide comprehensive email security.
Proton Calendar
Encrypted calendar functionality includes meeting scheduling, availability sharing, and team coordination features. The service integrates seamlessly with Proton Mail for streamlined meeting management while maintaining privacy protection for all scheduling data. Calendar sharing capabilities enable team coordination without compromising data security.
Proton Drive
Each user receives 1 TB of encrypted cloud storage (up from 500 GB in August 2024), with unlimited file sharing. The platform includes a real-time document collaboration editor, 365-day version history, and granular access controls for secure document management. All data stored in Proton Drive is end-to-end encrypted, protecting sensitive business files from unauthorized access.
Proton VPN Business
Users can access up to 10 VPN connections with global server coverage in 85+ countries. The service includes Secure Core servers for enhanced privacy protection and supports custom DNS configurations for business network requirements. Advanced security protocols and anti-censorship technology provide secure network access for remote teams. Organizations evaluating VPN options can compare Proton's integrated approach with dedicated business VPN solutions.
Proton Pass Enterprise
The integrated password manager provides unlimited password storage with 50 secure vaults per user. Features include built-in two-factor authentication, hide-my-email aliases, and team password sharing with detailed permission controls. For organizations comparing password management solutions, this integrated approach contrasts with standalone options detailed in our comprehensive business password manager comparison.
Security Architecture and Certifications
Proton's zero-access encryption ensures that user data remains inaccessible to unauthorized parties, including Proton itself. This approach protects against external threats and potential data requests from authorities, as encrypted data cannot be decrypted without user-controlled keys.
Recent Certification Achievements
SOC 2 Type II Certification (July 2025)
In July 2025, Proton achieved its first SOC 2 Type II certification, conducted by Schellman, an independent auditing firm. The SOC 2 Type II audit examined whether Proton had implemented strong security controls and whether those controls were consistently followed in practice across all operations. The audit process included interviews with staff, technical reviews of infrastructure, and detailed documentation assessments across access management, incident response, system monitoring, and risk assessment.
This certification provides third-party validation that Proton not only has strong security controls in place but that they're consistently followed in practice. The certification is particularly important for businesses in finance, healthcare, and other regulated industries where SOC 2 is often a baseline requirement before moving forward with a vendor.
ISO 27001 Certification (May 2024)
Achieved in May 2024, ISO 27001 is the international standard for information security management systems, providing best-practice guidance for managing data security. This certification demonstrates Proton's systematic approach to managing sensitive business information.
Regulatory Compliance
The platform maintains GDPR compliance under the Swiss Federal Act on Data Protection and supports HIPAA requirements for healthcare organizations. Switzerland's Federal Act on Data Protection (FADP) provides stronger privacy protections than many international frameworks, offering additional legal safeguards beyond technical encryption measures.
Multi-Layer Security Protection
The platform implements several security layers beyond fundamental encryption:
- Proton Sentinel Protection: AI-powered monitoring combined with human expertise identifies and blocks sophisticated attack attempts. Since its August 2023 launch, the system has documented thousands of attempted account takeovers that were prevented.
- Swiss Privacy Framework: Legal protection under some of the world's strictest privacy regulations, offering additional safeguards beyond technical encryption measures.
- Administrative Controls: Organizations can enforce security policies, including mandatory two-factor authentication, session management, and access monitoring across all services.
- Open Source Transparency: All Proton apps are open source, enabling independent verification that they function exactly as claimed.
For organizations seeking to understand the broader security landscape, our comprehensive cybersecurity guide for small businesses provides context on how encrypted productivity platforms fit into overall security strategies.
Try Proton Business Suite Free for 14 Days
No credit card required • Full feature access
Performance and Usability Assessment
User Experience Evaluation
Testing across desktop and mobile platforms reveals a mature interface that balances security with usability. While encryption processes introduce slight delays compared to unencrypted alternatives, performance remains within acceptable ranges for typical business workflows.
The web interface provides consistent functionality across services, with seamless transitions between email, calendar, and file management. Mobile applications maintain feature parity with desktop versions, ensuring a consistent user experience across devices.
Performance Metrics
| Service | Load Time | Sync Speed | Mobile Performance |
|---|---|---|---|
| 2-3 seconds | Real-time | Excellent | |
| Calendar | 1-2 seconds | Near real-time | Very Good |
| Drive | 3-4 seconds | Variable by file size | Good |
| VPN | 5-10 seconds connection | Depends on server location | Very Good |
| Pass | 1-2 seconds | Real-time sync | Excellent |
Migration Tools
The Easy Switch tool simplifies the transition process with automated import features, migrating data from Google Workspace, Microsoft 365, and other platforms with minimal user intervention. The migration process handles emails, contacts, and calendar entries, reducing the burden on IT teams during platform transitions.
Pricing Analysis and Value Assessment
Current Pricing Structure
Proton Business Suite: $12.99 per user monthly (annual billing) or $14.99 monthly
Includes:
- 1 TB storage per user (doubled from 500 GB in August 2024)
- 20 email addresses per user
- 15 custom domains
- All platform services (Mail, Calendar, Drive, VPN, Pass)
- Proton Scribe AI writing assistant
- Proton Sentinel security features
- Priority support with dedicated account management
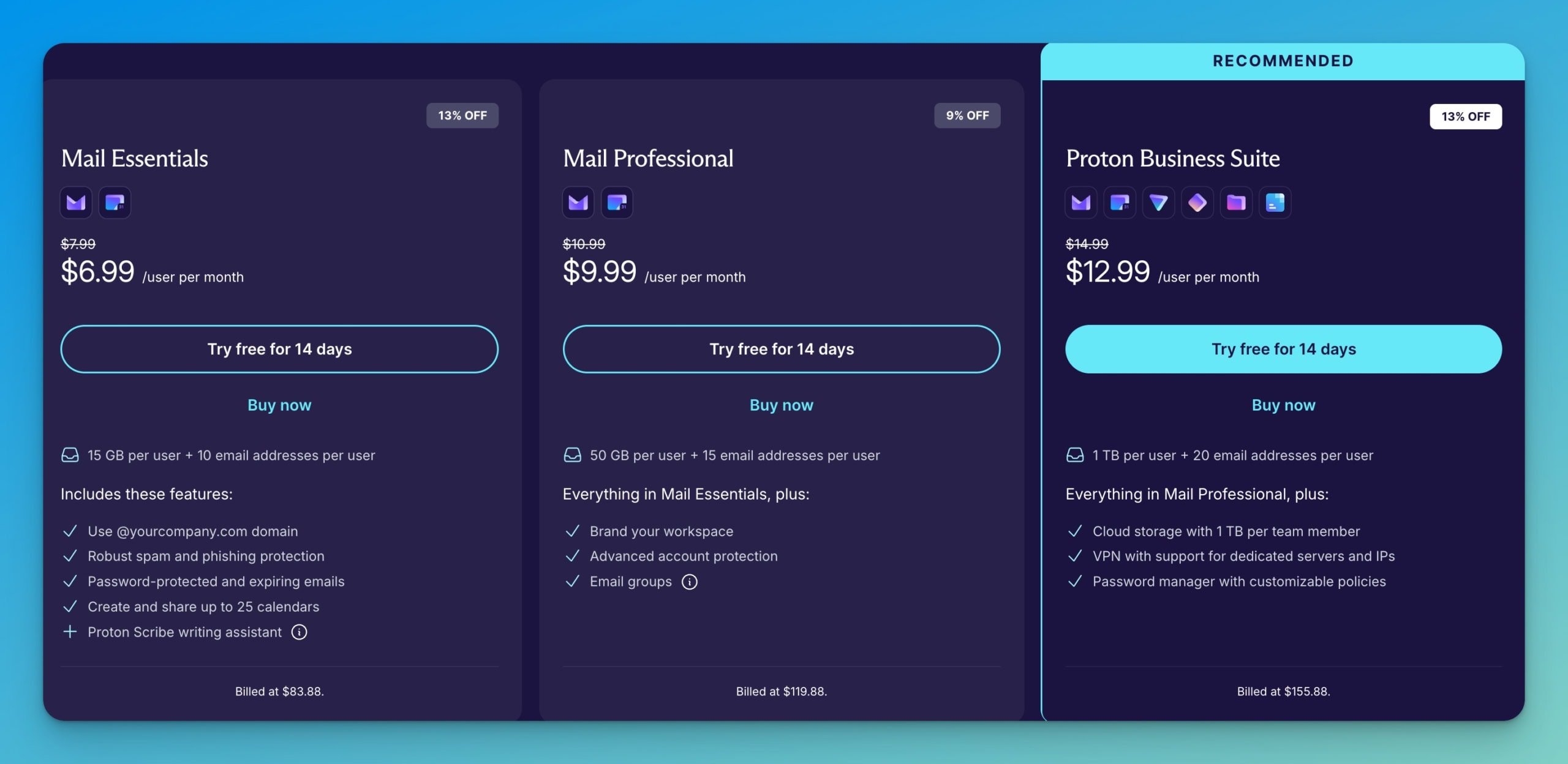
Alternative Plans
- Mail Essentials: $6.99 monthly for introductory encrypted email and calendar with 15 GB storage and 10 addresses per user
- Mail Professional: $9.99 monthly with enhanced features, 50 GB storage, and workspace branding
- Enterprise: Custom pricing for large organizations requiring dedicated support and customizable infrastructure
Competitive Comparison
| Platform | Monthly Cost | Storage | VPN Included | Password Manager | Encryption |
|---|---|---|---|---|---|
| Proton Business Suite | $12.99 | 1 TB | ✓ | ✓ | End-to-end |
| Google Workspace Business | $12.00 | 2 TB | ✗ | ✗ | At rest/transit |
| Microsoft 365 Business Premium | $12.50 | 1 TB | ✗ | ✗ | At rest/transit |
| Tutanota Business | $3.00 | 20 GB | ✗ | ✗ | End-to-end |
Proton Business Suite demonstrates competitive value when factoring in the costs of separate VPN and password management services. Organizations requiring standalone business VPN services or comprehensive password management solutions would typically spend $15-20 per user monthly for comparable features across multiple vendors.
Ready to experience comprehensive privacy protection?
No credit card required • 14-day free trial
Implementation Considerations
Technical Requirements
Organizations require modern web browsers for optimal platform access, mobile devices running recent operating systems, and administrative access to configure custom domains. Network infrastructure should support VPN integration for optimal security benefits.
Migration Process
Phase 1: Initial Setup (Weeks 1-2)
- Administrator account setup and domain verification
- Initial user provisioning and role assignment
- Basic training on platform navigation
- Security feature configuration (2FA, Sentinel)
Phase 2: Data Migration (Weeks 3-4)
- Automated data migration using the Easy Switch tool
- Email, calendar, and contact imports
- File migration to Proton Drive
- Password import to Proton Pass
- Testing and validation
Phase 3: Full Deployment (Month 2)
- VPN rollout for remote access
- Advanced feature implementation
- Comprehensive user training
- Documentation and support resources
- Ongoing optimization
Common Implementation Challenges
User Adaptation
Teams transitioning from mainstream platforms may need to adjust to privacy-focused tools that operate differently. Comprehensive training that emphasizes the security benefits helps overcome initial resistance. Setting realistic expectations about the learning curve prevents frustration during the transition period.
Feature Expectations
Teams may expect functionality identical to Google Workspace or Microsoft 365. Clear communication about privacy trade-offs versus convenience features prevents disappointment. Focus on what the platform does well rather than missing features.
Integration Limitations
Limited third-party integrations require workflow adjustments, though the platform's native capabilities well address core productivity needs. Organizations heavily reliant on specific third-party tools should verify compatibility before migration.
Real-World Application Analysis
Healthcare Sector Implementation
Organization: 25-employee medical practice
Challenge: HIPAA compliance requirements while maintaining efficient team collaboration
Solution: Proton Business Suite deployment focusing on encrypted patient communication and secure document sharing
Results:
- Enhanced compliance posture with end-to-end encryption
- Reduced audit concerns through demonstrable security controls
- Improved team collaboration without compromising patient privacy
- Cost savings from consolidated vendor relationships
Legal Industry Deployment
Organization: 15-attorney law firm
Challenge: Client confidentiality protection and secure mobile team access
Solution: Implementation emphasizing secure client communication and protected document sharing
Results:
- Improved client trust through demonstrable privacy protection
- Secure access from any location through VPN protection
- Simplified security management with a unified platform
- Enhanced attorney-client privilege protection
Technology Startup Adoption
Organization: 35-employee technology startup
Challenge: Intellectual property protection while scaling operations
Solution: Migration from Google Workspace using Easy Switch tools
Results:
- Enhanced security posture for proprietary development
- Cost-effective scaling through unified platform billing
- Improved team security practices
- Reduced vendor management overhead
Competitive Landscape Assessment
Advantages Over Mainstream Platforms
Proton Business Suite offers genuine end-to-end encryption by default, whereas platforms like Google Workspace and Microsoft 365 primarily provide encryption at rest and in transit. The unified approach eliminates multiple vendor relationships and ensures consistent privacy protection across all services.
The Swiss privacy law framework provides stronger legal protections than those offered by platforms operating under US jurisdiction, particularly relevant for international organizations or those handling sensitive data that require maximum privacy protection. The combination of SOC 2 Type II and ISO 27001 certifications demonstrates verifiable security practices rather than marketing claims.
Areas Where Alternatives Excel
Google Workspace and Microsoft 365 maintain advantages in third-party integration ecosystems, with thousands of available applications and services. These platforms also offer more advanced collaboration features and faster performance, thanks to lower encryption overhead.
Mainstream platforms benefit from larger development teams and faster feature rollouts, particularly for advanced productivity features beyond core email, calendar, and file sharing functionality. Organizations requiring extensive third-party integrations may find mainstream alternatives better suited to their needs.
Expert Recommendations
Ideal Use Cases
Privacy-Conscious Organizations
Organizations seeking genuine data privacy protection will find that Proton Business Suite delivers comprehensive encryption without compromising essential business functionality. The platform's privacy-by-design approach ensures protection across all services.
Regulated Industries
The healthcare, finance, and legal sectors benefit from the platform's privacy-by-design approach and Swiss legal framework to meet stringent compliance requirements. The SOC 2 Type II and ISO 27001 certifications provide third-party validation of security controls.
Remote-First Teams
Teams requiring secure communication and collaboration tools with integrated VPN access find that the unified platform approach simplifies security management while ensuring protection from any location.
Consider Alternatives When
Extensive Third-Party Integration Requirements
Organizations that require extensive third-party integrations may be better served by the Google Workspace or Microsoft 365 ecosystems, which offer broader application compatibility and development frameworks.
Budget Constraints Without Privacy Premium
Organizations without significant privacy concerns or regulatory requirements might find lower-cost alternatives sufficient, though the unified platform approach often provides better value when factoring in the costs of separate security services.
Advanced Collaboration Features
Organizations requiring advanced collaboration features beyond core productivity tools may find that mainstream platforms offer more robust functionality in areas such as real-time co-authoring and advanced document management.
Final Assessment
Proton Business Suite addresses the growing need for genuine privacy protection in business environments without sacrificing essential productivity functionality. The platform represents a mature alternative to mainstream productivity suites for organizations prioritizing data privacy and security.
The comprehensive encryption approach, unified platform design, and Swiss privacy framework create a compelling value proposition for privacy-conscious organizations. The recent achievement of SOC 2 Type II certification in July 2025, combined with existing ISO 27001 certification, demonstrates Proton's commitment to meeting enterprise security standards.
The storage capacity increased to 1 TB per user (doubled from 500 GB in August 2024) at no additional cost, demonstrating the platform's continued investment. The integration of features such as Proton Scribe AI and enhanced Proton Sentinel security demonstrates ongoing platform development.
While there are some convenience trade-offs compared to mainstream alternatives, the platform delivers on its core promise of protecting business data while maintaining productivity. For organizations evaluating productivity platforms in an era of increasing privacy awareness and regulatory requirements, Proton Business Suite merits serious consideration as a long-term solution that prioritizes user privacy over data monetization.
Organizations already invested in comprehensive business technology stacks should evaluate how Proton Business Suite fits into their overall infrastructure. The platform works well as a foundation for privacy-focused operations, particularly when combined with appropriate network security measures and regular security audit practices.
Final Rating: 4.2/5
Strengths: Comprehensive privacy protection, SOC 2 Type II and ISO 27001 certified, unified platform approach, competitive pricing with included security services, doubled storage capacity
Areas for Improvement: Third-party integration ecosystem, performance optimization, advanced collaboration features
Experience Proton Business Suite
Ready to prioritize privacy without sacrificing productivity?
Frequently Asked Questions
Is Proton Business Suite suitable for healthcare organizations?
Yes, Proton Business Suite meets HIPAA requirements and provides end-to-end encryption to help healthcare organizations maintain patient privacy. The SOC 2 Type II certification and Swiss privacy laws offer additional benefits to compliance. Organizations should conduct their own compliance assessments to ensure the platform meets their specific regulatory requirements.
How does Proton Business Suite compare to Google Workspace?
Proton Business Suite provides stronger privacy protection through end-to-end encryption by default, while Google Workspace offers more third-party integrations and advanced collaboration features. Proton includes VPN and password management at no additional cost, whereas Google Workspace requires separate subscriptions. Organizations prioritizing privacy typically prefer Proton, while those needing extensive integrations may prefer Google Workspace.
Can we migrate from Microsoft 365 to Proton Business Suite?
Yes, Proton provides the Easy Switch tool that automates migration from Microsoft 365, including emails, contacts, and calendar entries. The migration process typically takes 2-4 weeks, depending on data volume and organizational size. File migration can be manual or automated using third-party tools.
What happens to our data if we stop using Proton Business Suite?
You can export all data before canceling your subscription. Proton provides standard export formats for emails (MBOX, EML), calendars (ICS), and contacts (VCF). Files from Proton Drive can be downloaded individually or in bulk. After subscription cancellation, you have a grace period to export data before your account is closed.
Does Proton Business Suite work offline?
Email and calendar have limited offline functionality through mobile apps. Proton Drive requires an internet connection for file access. The platform is primarily designed for online use with encrypted synchronization across devices. Organizations requiring extensive offline access should plan accordingly.
How does Proton's Swiss jurisdiction affect data requests?
Swiss privacy laws provide strong protection against data requests. Law enforcement must go through Swiss courts, which apply strict privacy standards. Even if compelled, Proton's zero-access encryption prevents them from decrypting user data. This provides stronger protection than platforms operating under US jurisdiction.
Can we use our existing email client with Proton Mail?
Yes, Proton Mail supports IMAP/SMTP via the Proton Bridge, which maintains end-to-end encryption while allowing the use of clients like Outlook, Thunderbird, or Apple Mail. The Bridge application runs on your local machine and handles encryption/decryption.
What support options are available for Business Suite customers?
Business Suite includes priority support with dedicated account management. Support is available 24/7 through the customer service center. Enterprise customers receive additional support, including onboarding assistance and custom training. Proton's support earned recognition in Newsweek's “2025 Best Customer Service” rankings.
How does the AI writing assistant work with encryption?
Proton Scribe AI processes text locally on your device before encryption, maintaining end-to-end encryption throughout. The AI assistant helps with email composition, grammar checking, and professional communication while respecting privacy protections. Processing occurs client-side to prevent data exposure.
Can we customize storage allocation across users?
Administrators can reallocate storage from the 1 TB-per-user pool. For example, if one user needs 2 TB and another needs only 500 GB, storage can be redistributed. Organizations requiring more total storage can add users or upgrade to Enterprise plans with customizable storage options.
Disclosure: This review is based on the platform's current capabilities as of November 4, 2025. Pricing and features are subject to change. We may earn affiliate commissions from purchases made through our links, which helps support our independent testing and review process. Our recommendations are based on professional experience and testing.
For organizations seeking professional guidance on implementing secure productivity platforms, our team provides consultation services for businesses in South Florida. Learn more about our Miami-area IT security services.