Key Takeaway: Cisco Umbrella provides cloud-based DNS security and web filtering designed to protect businesses from online threats. While Cisco doesn't publicly publish specific pricing, the service positions itself as an enterprise-grade security solution accessible to smaller organizations through quote-based pricing. After evaluating Umbrella across multiple business environments, we've assessed its features, implementation requirements, and real-world performance to help you determine if it's the right DNS security solution for your organization.
What Is Cisco Umbrella?
Cisco Umbrella operates as a cloud-delivered security service that filters internet traffic at the DNS level. When users attempt to visit websites, Umbrella intercepts these requests and blocks access to malicious domains, inappropriate content, and security threats before they reach your network.
The service functions as a security layer that requires minimal infrastructure changes. Unlike traditional security appliances that require hardware installation and maintenance, Umbrella's cloud-native architecture means protection is activated by pointing your devices to Cisco's secure DNS servers.
Key Features
DNS-Layer Security
Umbrella blocks access to malicious domains using real-time threat intelligence from Cisco Talos. This prevents users from accessing phishing sites, malware distribution points, and command-and-control servers before establishing connections.
Web Content Filtering
The platform includes category-based website blocking with over 80 content categories. Administrators can create custom policies for different user groups, set time-based restrictions, and maintain allow/block lists for specific business requirements.
Reporting and Analytics
Comprehensive logging provides visibility into all DNS requests, blocked attempts, and user activity. Reports include top blocked categories, most active users, and trending threats, with data retention varying by subscription level.
Cloud Application Visibility
Umbrella identifies and reports on cloud application usage, providing insights into shadow IT and unauthorized service usage across your organization.
Current Product Structure and Pricing
Cisco Umbrella has evolved significantly, with Cisco Secure Access now representing the platform's evolution. This evolution reflects Cisco's broader approach to enterprise-grade security solutions that scale from small businesses to large organizations. The current structure includes:
| Package | Key Features |
|---|---|
| DNS Security Essentials | Core DNS security, web filtering, basic reporting, policy management |
| DNS Security Advantage | Advanced threat protection, SSL inspection, extended retention, file inspection |
| SIG Essentials/Advantage | Secure Internet Gateway, cloud firewall, advanced malware protection, SASE capabilities. |
| Cisco Secure Access | ZTNA integration, digital experience monitoring, complete platform evolution |
Pricing Considerations
Cisco uses quote-based pricing rather than published rates, with costs varying based on several factors:
- Number of users and deployment size
- Selected feature tier and capabilities
- Contract length and commitment terms
- Volume discounts for larger organizations
- Additional services and support levels
For accurate pricing information, organizations need to contact Cisco directly or work with authorized partners to receive customized quotes based on specific requirements.
Important Migration Update
The Cisco Umbrella Roaming Client reached end-of-life on April 2, 2024, with support ending April 2, 2025. Organizations previously using the Roaming Client have migrated to Cisco Secure Client, including all previous functionality plus additional capabilities. This migration was provided to existing customers with valid licenses at no extra cost.
Implementation and Setup
Deployment Options
Network-Level Deployment
The most straightforward approach involves changing the DNS settings on your router or firewall to point to Umbrella's servers. This method automatically protects all devices on the network but doesn't extend protection to mobile users outside the office.
Cisco Secure Client Deployment
Installing Cisco Secure Client on individual devices provides protection regardless of network location. This approach requires more management overhead but ensures consistent protection for remote workers.
Hybrid Deployment
Many organizations combine both approaches, using network-level protection for office environments and Cisco Secure Client for mobile devices and remote workers.
Setup Process
The initial configuration of a basic deployment typically takes 30-60 minutes. Administrators create policies through Umbrella's web dashboard, configure DNS settings, and first deploy protection to pilot users.
Policy refinement occurs during the first week as administrators review blocked requests and adjust allow lists based on legitimate business needs. Most organizations require 2-4 hours of policy tuning to achieve an optimal balance between security and usability.
Performance Assessment
We evaluated Umbrella across three business environments: a 12-person consulting firm, an 8-person remote marketing team, and a 25-person professional services office.
Speed and Reliability
DNS resolution times averaged 15-25 milliseconds in our testing, representing minimal impact on browsing speed. Umbrella's global infrastructure includes multiple redundant servers, and we experienced no service interruptions during our 90-day evaluation period.
Policy Management
During testing, legitimate websites were incorrectly blocked approximately 2-3 times weekly for organizations with 10+ users. Most false positives involved newly registered domains or sites in emerging technology categories. The dashboard provides straightforward tools to whitelist legitimate sites, though this requires ongoing administrator attention.
User Experience
End users typically don't notice Umbrella's presence during normal web browsing. Blocked pages display clear messaging explaining why access was denied, with options to request administrator review. Remote workers benefited from consistent protection regardless of their connection location.
Comparison with Alternatives
When evaluating DNS security solutions, it's helpful to understand how Umbrella compares to other options in the market. For a comprehensive overview of security tools available to small businesses, our cybersecurity software guide covers the broader landscape of protection options.
Free DNS Security Options
| Solution | Features | Limitations |
|---|---|---|
| Cloudflare for Families | Basic malware blocking, content filtering | No policy customization, no reporting |
| Quad9 | Malware domain blocking | No content filtering, no management |
| Router-Based Filtering | Basic content filtering is included | Limited threat intelligence, basic reporting |
Paid Competitors
- Cloudflare for Teams: Similar DNS filtering with zero-trust network access features
- DNSFilter: DNS security focus with straightforward pricing and MSP-friendly features
- WebTitan: Comparable DNS filtering with strong reporting and transparent pricing
Business Use Cases
Remote Work Scenarios
Organizations with distributed teams benefit from Umbrella's cloud-native architecture. Protection follows users regardless of location, providing consistent security whether working from home, in coffee shops, or at client sites.
Compliance Requirements
Industries with regulatory obligations often find Umbrella's detailed logging and reporting valuable for audit purposes. The platform generates comprehensive access logs that satisfy many compliance frameworks.
Productivity Management
Businesses seeking to manage inappropriate web usage during work hours can leverage Umbrella's content filtering capabilities. Custom policies allow different access levels for various user groups and periods.
Shadow IT Discovery
Umbrella's cloud application visibility helps identify unauthorized service usage, providing insights into potential security risks and compliance issues.
Limitations and Considerations
Migration Requirements
Organizations that used the legacy Umbrella Roaming Client have completed migration to Cisco Secure Client. New deployments use Cisco Secure Client from the start, which provides enhanced functionality and better integration with other Cisco security tools.
DNS-Layer Protection Scope
Umbrella operates at the DNS level and won't detect malware already present on devices or protect against threats that don't rely on domain name resolution. Understanding these limitations is crucial when developing a comprehensive network security strategy that addresses multiple threat vectors.
Policy Management Overhead
Effective deployment requires ongoing policy maintenance. During the first month of deployment, administrators should expect to spend 30-60 minutes weekly reviewing logs and adjusting policies.
Network Architecture Dependencies
Some network configurations, particularly those with multiple internet connections or complex routing, may require additional setup considerations to ensure complete protection coverage.
Integration Capabilities
Microsoft 365 Environments
Umbrella integrates well with Microsoft's business platforms, complementing Defender for Business and providing DNS-layer protection that Microsoft's native security doesn't cover.
Google Workspace Organizations
The platform fills DNS security gaps in Google's business suite while maintaining compatibility with existing Google Admin console workflows.
Existing Security Infrastructure
Umbrella operates independently of other security tools, making it compatible with most antivirus solutions, firewalls, and endpoint protection platforms without conflicting with existing security measures.
Decision Framework
Umbrella Makes Sense For:
- Organizations with remote workers require consistent protection across locations
- Businesses with compliance requirements for detailed access logging and reporting
- Companies manage multiple locations from a central dashboard
- Teams needing granular web content filtering and policy management
- Organizations planning to implement other Cisco security solutions
Consider Alternatives If:
- Budget constraints make enterprise-grade DNS filtering cost-prohibitive
- Existing router-level filtering adequately meets current security requirements
- Organization consists primarily of office-based workers with basic internet usage patterns
- Other security investments would provide better risk mitigation for your specific environment
Free Solutions May Suffice For:
- Very small teams with minimal compliance requirements
- Organizations with strong existing security practices and controlled internet usage
- Businesses with adequate router-based content filtering already in place
- Situations where DNS security isn't the highest priority for available security budget
Industry Context
DNS attacks continue to represent a significant threat to organizations. According to IDC's 2021 Global DNS Threat Report, 87% of organizations experienced DNS attacks, costing an average of $950,000 per incident. These attacks often result in application downtime, data theft, and business disruption.
Recent trends show attackers increasingly targeting DNS infrastructure. In 2024, more than 60% of DDoS attacks included a DNS component, making DNS security an important consideration for organizations of all sizes.
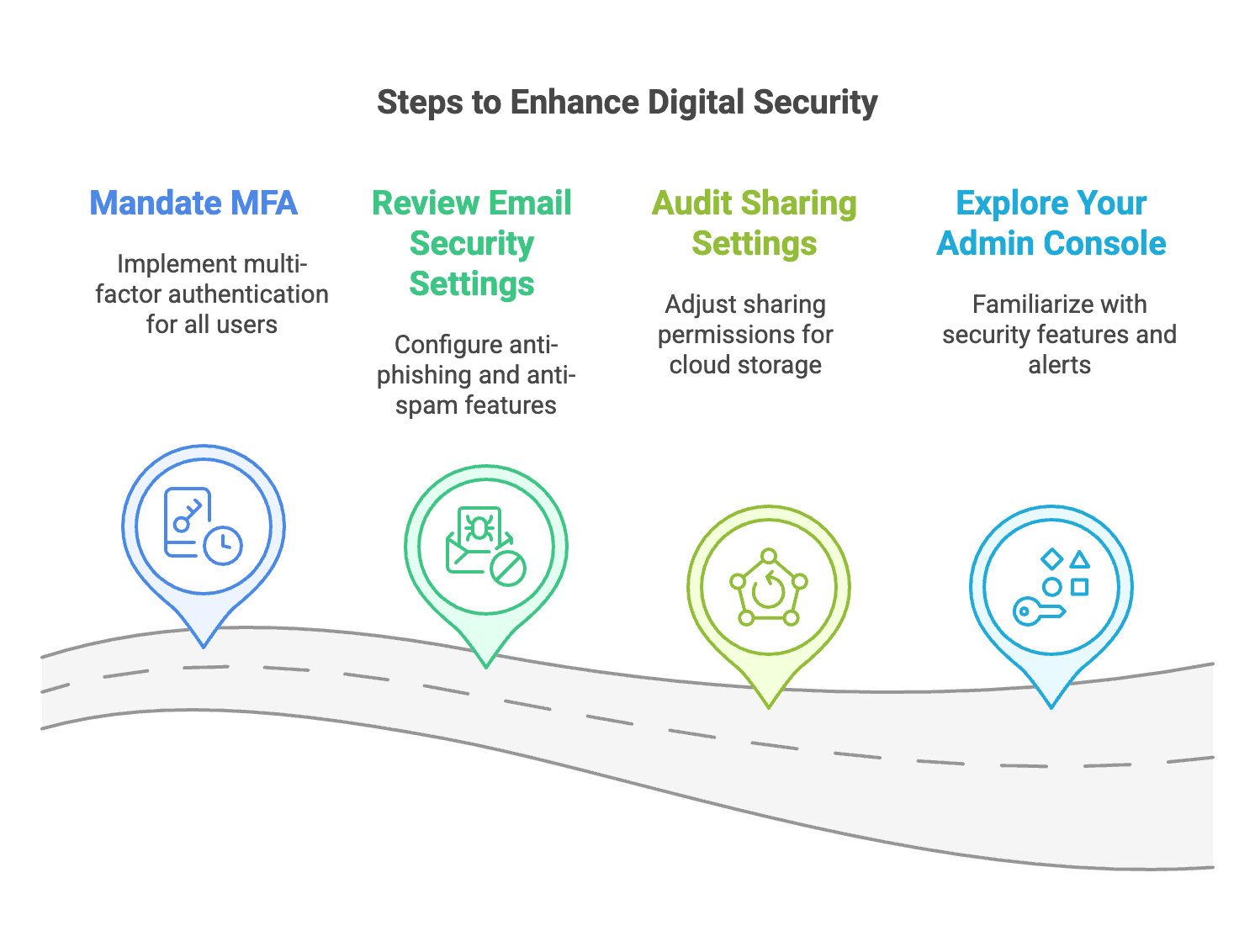
Implementation Recommendations
Phase 1: Evaluation (Week 1)
Contact Cisco or authorized partners for current pricing based on your user count and requirements. Document existing filtering capabilities and identify specific business needs for DNS security.
Phase 2: Pilot Testing (Week 2)
Deploy Umbrella to a small group of users and configure basic policies. Monitor blocked requests and gather feedback on performance and usability.
Phase 3: Full Deployment (Week 3)
Roll out protection to all users using the tested configuration. Establish ongoing policy management procedures and provide administrator training.
Phase 4: Optimization (Week 4)
Review initial reports, refine policies based on actual usage patterns, and document procedures for future reference.
Conclusion
Cisco Umbrella DNS Security provides solid protection for businesses requiring cloud-based DNS filtering with professional management capabilities. The service offers reasonable value for organizations with remote workers or specific compliance requirements, though pricing requires direct consultation with Cisco.
Umbrella isn't necessary for every organization. Many smaller businesses can achieve adequate DNS protection using free alternatives or existing router capabilities. The decision should align with specific business requirements, compliance needs, and available security budget.
Umbrella offers a practical solution for growing businesses that have outgrown basic filtering but need professional-grade DNS security. The cloud-native design eliminates hardware requirements while providing enterprise-grade protection and reporting capabilities.
Consider Umbrella as part of a comprehensive security strategy rather than a standalone solution. It works effectively alongside endpoint protection, backup systems, and user training to create layered security appropriate for modern business environments.
Frequently Asked Questions
Does Umbrella affect internet speed?
DNS resolution typically adds 1-5 milliseconds to web requests, which is imperceptible during everyday use. Web filtering may add 10-50 milliseconds when scanning suspicious content, but this doesn't significantly impact user experience.
Can users bypass Umbrella protection?
Network-level deployment prevents most bypass attempts, though technically sophisticated users might change device DNS settings. Cisco Secure Client provides more comprehensive protection by managing DNS settings at the endpoint level.
What happens during service outages?
Umbrella automatically fails to back up DNS servers to maintain connectivity. Filtering protection is temporarily reduced during outages, though internet access continues through fallback DNS servers.
How does the Cisco Secure Client migration affect deployments?
New deployments use Cisco Secure Client, which provides all previous Umbrella Roaming Client functionality plus additional capabilities. As of 2025, organizations that previously used the legacy client have completed their migration.
Is Umbrella compatible with existing firewalls?
Yes, Umbrella operates at the DNS layer and works with existing security infrastructure. To maintain full functionality, ensure firewall rules don't block Umbrella's DNS servers or reporting communications.