Published: December 14, 2022 | Last updated: September 2025
Key Takeaway: Business IT security requires a multi-layered approach combining technical controls, employee education, and regular monitoring. These seven proven strategies help small and medium businesses build robust defenses against evolving cyber threats while maintaining operational efficiency.
Modern businesses face an increasingly complex threat landscape where cyber attacks have become more sophisticated and frequent. From ransomware targeting small businesses to advanced persistent threats infiltrating enterprise networks, the stakes have never been higher. A comprehensive IT security strategy protects not only your data and systems but also your reputation, customer trust, and business continuity.
The challenge for many business owners lies in knowing where to focus their security efforts and resources. While technology continues to evolve, the fundamental principles of effective IT security remain consistent: defense in depth, proactive monitoring, and continuous improvement.
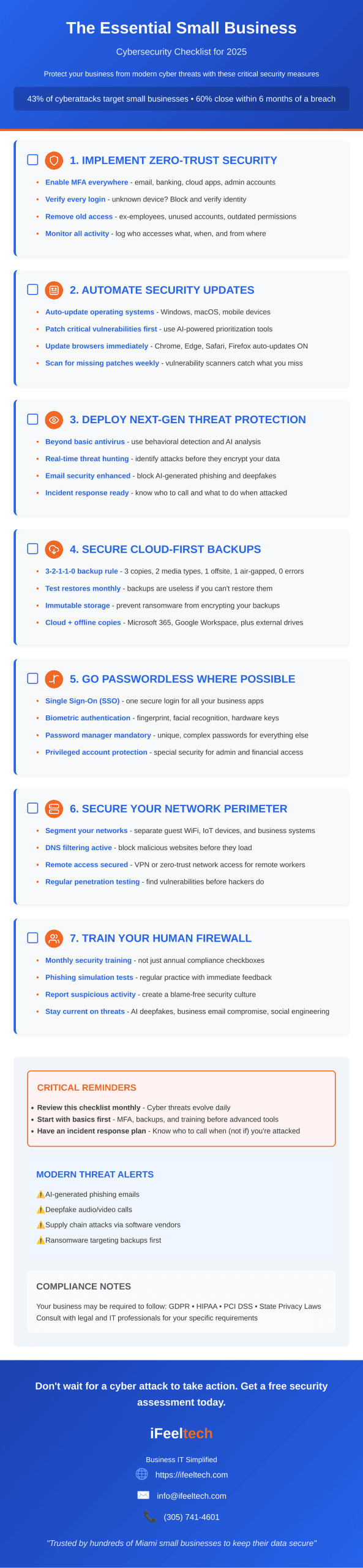
1. Conduct Comprehensive Security Audits and Risk Assessments
Regular security audits form the foundation of any effective IT security program. Unlike basic vulnerability scans, comprehensive audits examine your entire security posture, including policies, procedures, technical controls, and human factors.
What a Thorough Security Audit Should Include
Network Infrastructure Review: Examine firewall configurations, network segmentation, wireless security, and access controls across all network entry points.
Endpoint Assessment: Evaluate security software deployment, patch management processes, and device compliance across workstations, servers, and mobile devices.
Data Protection Analysis: Review data classification, encryption implementations, backup procedures, and access controls for sensitive information.
Policy and Compliance Evaluation: Assess security policies, employee training records, incident response procedures, and regulatory compliance status.
The most effective approach combines automated vulnerability scanning tools with manual penetration testing and policy reviews. Professional security audits should be conducted quarterly for critical systems and annually for comprehensive organizational assessments.
- Schedule vulnerability scans monthly for internet-facing systems
- Conduct penetration testing annually or after major system changes
- Review and update security policies quarterly
- Document all findings and track remediation progress
- Engage third-party security firms for objective assessments
2. Implement Advanced Authentication and Access Controls
Traditional password-only authentication has become insufficient against modern attack methods. Advanced authentication strategies combine multiple factors and intelligent access controls to create robust barriers against unauthorized access.
Multi-Factor Authentication (MFA) Implementation
Deploy MFA across all business-critical systems, starting with administrative accounts, email systems, and cloud services. Modern MFA solutions offer various authentication factors including smartphone apps, hardware tokens, biometric verification, and SMS codes.
Zero Trust Access Architecture
Implement zero trust principles where no user or device is automatically trusted, regardless of location or network connection. This approach requires continuous verification and limits access to only necessary resources.
Privileged Access Management
Establish separate administrative accounts with elevated privileges, implement just-in-time access for sensitive operations, and maintain detailed logs of all privileged activities.
Disclosure: iFeelTech participates in affiliate programs. We may earn a commission when you purchase through our links at no additional cost to you. Our recommendations are based on professional experience and testing.
For comprehensive password management across your organization, consider enterprise solutions like 1Password Business, which provides centralized password policies, secure sharing capabilities, and detailed access reporting.
Effective password security policies should mandate unique, complex passwords for each account, regular password updates, and immediate credential changes when employees leave the organization.
3. Deploy Comprehensive Backup and Disaster Recovery Solutions
Data backup has evolved far beyond simple file copying. Modern backup strategies must address ransomware attacks, insider threats, natural disasters, and system failures while ensuring rapid recovery capabilities.
3-2-1-1 Backup Strategy
Maintain three copies of critical data: the original plus two backups. Store backups on two different media types, keep one backup offsite, and ensure one backup remains offline (air-gapped) to protect against ransomware.
Automated Backup Verification
Implement automated systems that regularly test backup integrity, verify restoration procedures, and alert administrators to any backup failures or data corruption issues.
Recovery Time and Point Objectives
Define specific Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) for different types of data and systems, then design backup solutions that meet these requirements.
| Data Type | Backup Frequency | Retention Period | Recovery Target |
|---|---|---|---|
| Critical Business Data | Hourly/Real-time | 7 years | 15 minutes |
| User Files | Daily | 3 years | 4 hours |
| System Configurations | Weekly | 1 year | 24 hours |
| Archive Data | Monthly | Permanent | 72 hours |
Enterprise backup solutions like Acronis Cyber Protect provide integrated backup, anti-malware, and disaster recovery capabilities specifically designed to defend against ransomware attacks.
4. Establish Multi-Layered Network Security Architecture
Modern network security requires multiple defensive layers that work together to detect, prevent, and respond to various types of cyber threats. A single security appliance or software solution cannot address the full spectrum of network-based attacks.
Next-Generation Firewall (NGFW) Deployment
Deploy firewalls that provide deep packet inspection, application awareness, intrusion prevention, and threat intelligence integration. Configure rules based on business requirements rather than default permissive policies.
Network Segmentation Strategy
Implement network segmentation to isolate critical systems, limit lateral movement during security incidents, and contain potential breaches. Create separate network zones for different business functions and security levels.
Intrusion Detection and Response
Deploy network monitoring systems that can identify suspicious activities, unauthorized access attempts, and potential data exfiltration. Ensure these systems integrate with your incident response procedures.
For businesses seeking comprehensive network security solutions, enterprise security platforms often provide integrated firewall, intrusion prevention, and network monitoring capabilities in unified management consoles.
- Implement default-deny firewall policies with explicit allow rules
- Deploy endpoint detection and response (EDR) solutions
- Use network access control (NAC) for device authentication
- Monitor network traffic for anomalous patterns and behaviors
- Maintain updated threat intelligence feeds and signatures
5. Implement Advanced Endpoint Protection and Management
Traditional antivirus software provides insufficient protection against modern malware and sophisticated attack techniques. Advanced endpoint protection combines multiple detection methods, behavioral analysis, and automated response capabilities.
Endpoint Detection and Response (EDR)
EDR solutions provide continuous monitoring of endpoint activities, advanced threat detection using machine learning and behavioral analysis, and automated response capabilities to contain and remediate threats.
Unified Endpoint Management (UEM)
Implement centralized management systems that can deploy security policies, manage software updates, enforce compliance requirements, and remotely troubleshoot issues across all devices.
Application Control and Whitelisting
Deploy application control solutions that prevent unauthorized software execution, restrict administrative privileges, and maintain detailed logs of all software installations and modifications.
Enterprise endpoint security solutions like Bitdefender Business Security provide comprehensive protection including anti-malware, web protection, email security, and advanced threat detection capabilities.
Mobile Device Considerations
With remote work becoming standard, mobile device management has become critical. Implement mobile device management (MDM) solutions that can enforce security policies, remotely wipe lost devices, and separate business data from personal information on employee devices.
6. Develop Comprehensive Security Awareness and Training Programs
Human error remains one of the most significant security vulnerabilities in any organization. Effective security awareness programs go beyond annual training sessions to create ongoing education and security-conscious culture throughout the organization.
Phishing Simulation and Education
Conduct regular phishing simulation exercises that test employee responses to various types of social engineering attacks. Use simulation results to provide targeted training and measure improvement over time.
Role-Based Security Training
Develop training programs tailored to specific job functions and security responsibilities. Administrative staff require different security knowledge than general users or executives.
Incident Reporting and Response Training
Train employees to recognize potential security incidents and understand proper reporting procedures. Create clear escalation paths and ensure employees feel comfortable reporting suspicious activities without fear of blame.
| Training Topic | Frequency | Target Audience | Delivery Method |
|---|---|---|---|
| General Security Awareness | Quarterly | All Employees | Online modules |
| Phishing Recognition | Monthly | All Employees | Simulations + feedback |
| Administrative Security | Bi-annually | IT Staff | Hands-on workshops |
| Incident Response | Annually | Management | Tabletop exercises |
- Create security awareness campaigns with regular reminders and updates
- Recognize and reward employees who demonstrate good security practices
- Develop clear, easy-to-follow security policies and procedures
- Provide immediate feedback and additional training for security mistakes
- Include security responsibilities in job descriptions and performance reviews
7. Establish Continuous Monitoring and Incident Response Capabilities
Effective cybersecurity requires continuous monitoring of systems, networks, and user activities to detect potential threats before they cause significant damage. Modern threat actors often remain undetected in networks for months, making continuous monitoring essential for early detection and response.
Security Information and Event Management (SIEM)
Deploy SIEM solutions that aggregate security logs from multiple sources, correlate events to identify potential threats, and provide automated alerting for suspicious activities. Modern SIEM platforms use machine learning to reduce false positives and improve threat detection accuracy.
24/7 Security Operations Center (SOC)
Establish continuous monitoring capabilities either through internal security teams or managed security service providers. SOC services provide round-the-clock threat monitoring, incident analysis, and initial response coordination.
Automated Incident Response
Implement security orchestration, automation, and response (SOAR) platforms that can automatically respond to common security incidents, reducing response times and ensuring consistent incident handling procedures.
For comprehensive threat monitoring and response, solutions like NordLayer Zero Trust provide integrated network monitoring, threat detection, and automated response capabilities designed for modern distributed work environments.
Incident Response Plan Development
Create detailed incident response procedures that define roles and responsibilities, communication protocols, evidence preservation requirements, and recovery procedures for different types of security incidents.
Regular Response Testing and Improvement
Conduct tabletop exercises and simulated incident response scenarios to test procedures, identify gaps, and improve response capabilities. Update incident response plans based on lessons learned and evolving threat landscapes.
Threat Intelligence Integration
Incorporate threat intelligence feeds that provide information about emerging threats, attack techniques, and indicators of compromise relevant to your industry and organization.
Frequently Asked Questions
How often should small businesses conduct security audits?
Small businesses should conduct basic security assessments quarterly and comprehensive audits annually. Organizations in regulated industries or those handling sensitive data may need more frequent assessments. Monthly vulnerability scans for internet-facing systems are recommended regardless of business size.
What's the difference between traditional antivirus and modern endpoint protection?
Traditional antivirus relies primarily on signature-based detection of known malware, while modern endpoint protection uses behavioral analysis, machine learning, and advanced threat detection techniques to identify previously unknown threats. EDR solutions also provide incident response capabilities and detailed forensic information.
How can businesses balance security requirements with employee productivity?
Effective security implementations focus on seamless user experiences through single sign-on solutions, automated security controls, and risk-based authentication that adjusts security requirements based on context. Employee training and clear security policies help reduce friction while maintaining protection.
What should businesses do immediately after discovering a security incident?
Immediately isolate affected systems to prevent further damage, document all observations and actions taken, notify relevant stakeholders according to your incident response plan, and engage cybersecurity professionals if internal expertise is insufficient. Avoid attempting to “fix” systems before proper forensic analysis.
How much should small businesses budget for cybersecurity?
Industry recommendations suggest allocating 3-10% of IT budgets to cybersecurity, with higher percentages for businesses handling sensitive data or operating in regulated industries. Consider both technology costs and ongoing operational expenses including training, monitoring services, and incident response capabilities.
Can managed security services replace internal IT security capabilities?
Managed security services can provide expertise and 24/7 monitoring capabilities that many small businesses cannot maintain internally. However, organizations still need internal security awareness, policy development, and coordination capabilities. The best approach often combines managed services with internal security leadership and oversight.
Building a Sustainable Security Program
Implementing these seven essential security measures creates a strong foundation for protecting your business against cyber threats. However, cybersecurity is not a one-time implementation but an ongoing process that requires continuous attention, regular updates, and adaptation to emerging threats.
Start with the fundamentals: conduct a thorough security assessment, implement strong authentication controls, and establish reliable backup procedures. Build from there by adding advanced monitoring capabilities, comprehensive employee training, and sophisticated endpoint protection as your security program matures.
Remember that the most effective security programs balance technical controls with human factors, policy development with practical implementation, and proactive prevention with reactive response capabilities. Regular testing, continuous improvement, and staying informed about emerging threats will help ensure your security investments provide lasting protection for your business.
For organizations ready to take the next step in their cybersecurity journey, our comprehensive IT security checklist provides detailed implementation guidance and helps prioritize security investments based on your specific business requirements and risk profile.