Brace Yourself: Windows 10 Support Ends in 2025 – What Businesses and Techies Need to Know The countdown is on. While it may seem like a distant concern, Microsoft will officially end support for its widely used Windows 10 operating system on October 14, 2025. This means that your business or personal devices running Windows […]
Don't Pay the Ransom: How to Outsmart Cybercriminals and Protect Your Data Ransomware attacks are a nightmare for businesses of all sizes. These cybercriminals encrypt your vital company data, threatening to destroy it unless you pay a hefty ransom. Recently, these attacks have become more frequent, sophisticated, and costly. The average ransom demand skyrocketed in […]
QuickBooks Online has revolutionized small business accounting. Due to its convenience and flexibility, it has become a popular choice, which also makes it a prime target for cybercriminals. Data breaches can have devastating consequences, from financial losses to damaged reputations. That's why, in 2024, a robust QuickBooks Online security strategy is more important than ever […]
Imagine a workday transformed: video conferences flow effortlessly, massive files transfer in the blink of an eye, and online collaboration feels as smooth as in-person meetings. A strategic office network upgrade unlocks this potential. Ready to boost your team's efficiency and streamline workflows? Let's explore ethernet cables and data transmission to optimize your network. This […]
Data loss, whether caused by accidental deletion, hardware failure, or targeted cyberattacks, carries serious consequences for businesses. The cost of downtime and the potential damage to reputation can be devastating. As ransomware attacks grow in frequency and sophistication, traditional backup methods are proving increasingly vulnerable. This article examines why once-reliable data recovery strategies are insufficient […]
The Small Business Cybersecurity Guide: Essential Strategies for 2024 Forget giant corporations making headlines; cybercriminals are increasingly turning their attention towards small businesses. Why? Because small businesses often represent easy targets with outdated defenses and a limited understanding of the threats they face. The year 2024 has seen a rise in sophisticated attacks, from AI-driven […]
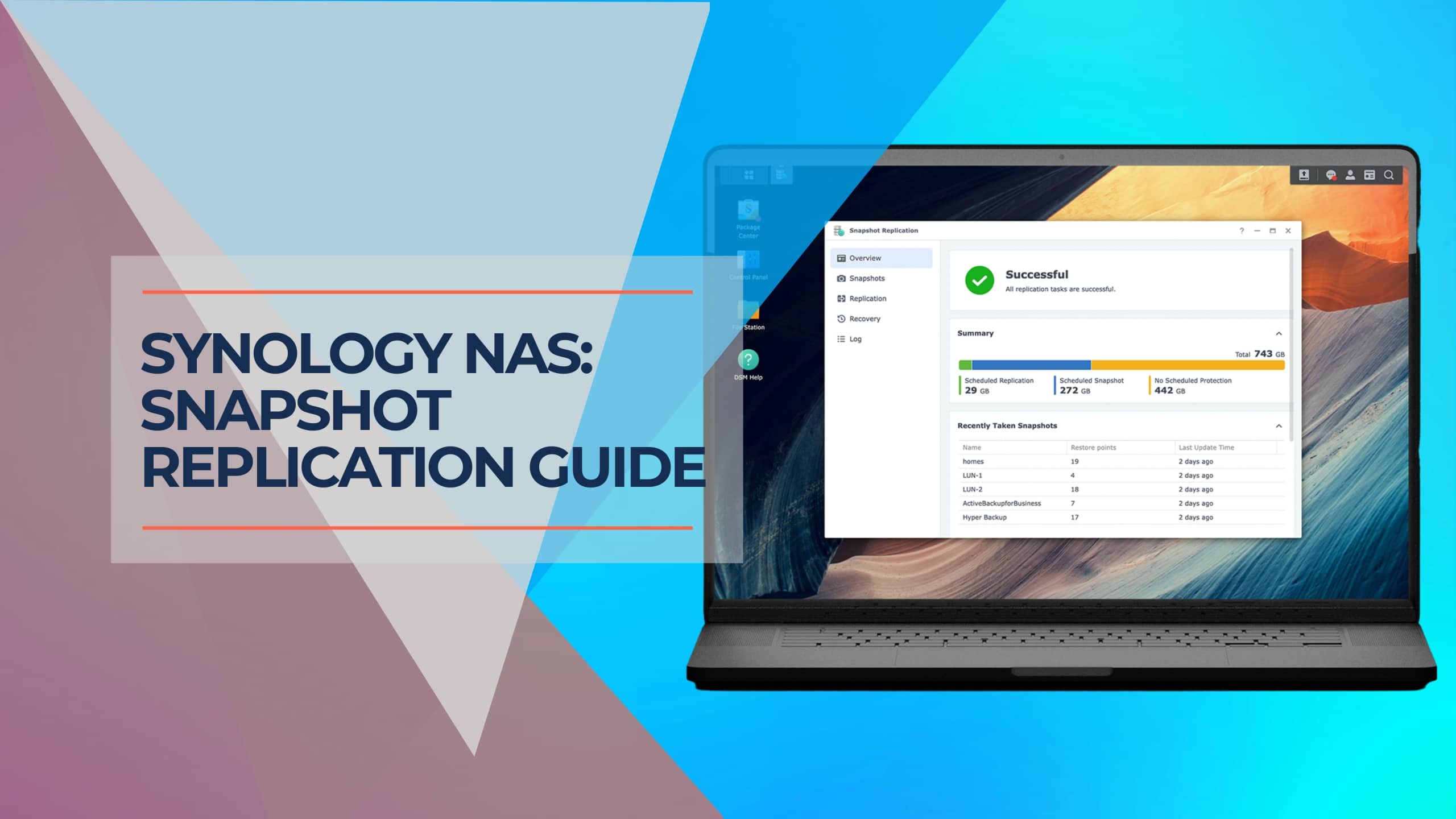
If you own a Synology NAS, you understand the importance of safeguarding your important data. Accidental deletions, surprise ransomware attacks, and hidden file corruption can all pose a risk. That's where Synology Snapshots shine. Think of snapshots as point-in-time backups of your files and folders. They offer a powerful way to rewind your NAS to […]
Choosing the Right Cables for Your Network Your business relies on its network for everything from email and file sharing to powering cloud-based applications. It's the invisible infrastructure that keeps your operations running smoothly. So, imagine this: slow file transfers, lagging video conferences, and constant downtime due to unreliable connections. These issues can directly translate […]
The workplace has undergone a permanent transformation. Remote and hybrid work models are here to stay, offering businesses and employees greater flexibility. However, this shift has exposed a critical vulnerability: cybersecurity. With employees accessing company data from various locations, often using personal devices and less secure home networks, the risk of cyberattacks has significantly increased. […]
Hey there, business owner! Are you considering switching from QuickBooks Desktop to QuickBooks Online? It's a smart move! QuickBooks Online offers many advantages, like accessing your data from anywhere, automatic backups, and a host of new features. Let's be real for a second – I used to get a little anxious about migrating QuickBooks as […]