Key Takeaway: Small businesses face significant cyber threats but lack accessible assessment tools. This comprehensive guide explores free cybersecurity evaluation options, focusing on privacy-first tools like Valydex that provide actionable insights without requiring technical expertise or data sharing.
Understanding Modern Cybersecurity Threats
Cybersecurity assessments have evolved from enterprise-only security audits to essential business tools accessible to organizations of all sizes. Current data indicates that 46% of cyber breaches target businesses with fewer than 1,000 employees, while 37% of ransomware attacks specifically affect companies with fewer than 100 employees. Small businesses face these threats while operating with limited security budgets and expertise.
The challenge lies not in recognizing the need for cybersecurity assessment, but in finding evaluation tools that provide actionable insights without requiring significant upfront investment or technical expertise. Our enterprise security solutions guide provides advanced protection strategies for businesses looking to implement comprehensive security measures that build upon proper assessment foundations.
What Constitutes a Comprehensive Security Assessment
A cybersecurity assessment evaluates an organization's current security posture against established frameworks and best practices. Unlike security audits, which focus on compliance verification, assessments provide actionable intelligence about vulnerabilities, risks, and improvement opportunities across technological and procedural security controls.
Modern Assessment Framework: NIST CSF 2.0
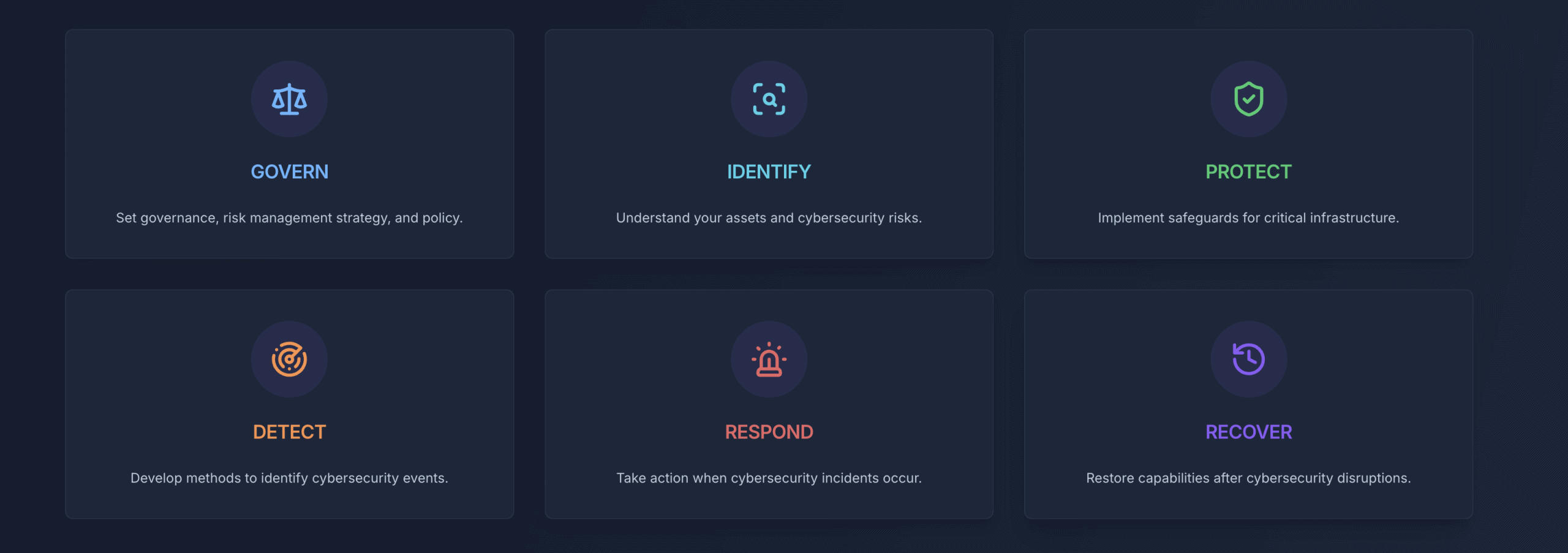
Modern cybersecurity assessments typically evaluate six core areas aligned with the NIST Cybersecurity Framework 2.0, released in February 2024. Our NIST CSF 2.0 cybersecurity tools guide provides detailed implementation guidance for businesses implementing these standards.
Governance and Risk Management
Leadership oversight, security policies, and risk tolerance alignment with business objectives. This includes evaluating whether security decisions integrate with business planning and whether organizations maintain appropriate oversight of security investments and outcomes.
Asset Identification and Management
Comprehensive inventory of hardware, software, data, and personnel assets. During this evaluation, organizations often discover unknown or unmanaged assets, with research indicating that businesses commonly underestimate their technology footprint by approximately one-third.
Protective Controls
Technical and administrative safeguards, including access controls, data protection measures, employee training programs, and protective technology deployment. This encompasses both preventive measures and the procedures that support their effective operation.
Detection Capabilities
Systems and processes for identifying security events, monitoring network activity, and maintaining situational awareness of potential threats. Modern detection capabilities span from automated monitoring tools to human-driven threat hunting activities.
Response Planning
Documented procedures for handling security incidents, including escalation protocols, communication strategies, and coordination mechanisms. Effective response planning reduces incident impact and recovery time significantly.
Recovery and Resilience
Business continuity capabilities, backup systems, and organizational learning processes that enable rapid restoration of normal operations following security incidents.
Current Threat Landscape and Assessment Drivers
Recent research reveals concerning trends that underscore the importance of regular security assessment for small businesses:
- AI-Enhanced Threat Growth: Cybersecurity attacks leveraging artificial intelligence increased by 135% in 2025, with 81% of cybercriminals now using AI-powered tools to improve attack success rates
- Ransomware-as-a-Service Expansion: The availability of ransomware tools has grown by 60% in 2025, making it easier for less technical criminals to launch attacks against small businesses
- Financial Impact: The average cost of a cyberattack on small businesses ranges from $120,000 to $1.24 million in 2025, with studies indicating that 60% of breached small businesses shut down within six months
- Supply Chain Vulnerabilities: Supply chain attacks have increased by 431% between 2021 and 2023, with 15% of small business breaches in 2025 originating from compromised vendors
Regular cybersecurity assessment serves as a foundational risk management practice. Research indicates that organizations with formal assessment processes demonstrate 12.7% higher likelihood of security success and 10.5% average improvement in security outcomes compared to those without systematic evaluation.
Assessment Types and Methodologies
Self-Assessment Tools
Self-assessment tools represent the most accessible option for small businesses. These tools provide automated evaluation through questionnaires and configuration checks. They typically require 15-60 minutes to complete and generate immediate results with prioritized recommendations.
Professional Security Assessments
Professional assessments involve qualified security consultants conducting comprehensive evaluations, including technical testing, policy review, and risk analysis. Based on a 2025 market analysis, these assessments typically cost $5,000-$15,000 for small businesses with under 50 employees. For organizations considering professional support, our managed IT services include ongoing security assessment and monitoring.
Automated Security Scanning
Automated scanning focuses specifically on identifying technical vulnerabilities through network scanning, web application testing, and configuration analysis. These tools can identify security weaknesses but lack the business context necessary for prioritizing remediation efforts effectively.
Continuous Monitoring Platforms
Continuous monitoring provides ongoing security posture visibility through real-time monitoring, threat intelligence integration, and automated compliance checking. While powerful, these platforms typically require dedicated security expertise to implement and manage effectively.
Evaluating Free Assessment Options
Key Features of Quality Assessment Tools
Framework Alignment: Effective cybersecurity assessments align with established security frameworks rather than vendor-specific checklists. The NIST Cybersecurity Framework 2.0 provides the most comprehensive foundation for small business assessment because it addresses both technical controls and business governance requirements across all six core functions.
Privacy and Data Protection: Assessment tools should minimize data collection and clearly explain how collected information is used. The most trustworthy options perform evaluations without requiring personal business information or storing assessment results on external servers.
Actionable Recommendations: Quality assessments translate technical findings into specific business actions with clear implementation guidance. Rather than generic advice like “improve password security,” practical tools provide step-by-step instructions for implementing specific security controls. Our business password manager guide offers detailed implementation guidance for this critical security control.
Common Limitations of Free Assessment Tools
- Limited Technical Validation: Many free assessments rely entirely on self-reported information without technical verification of security controls
- Vendor Bias: Assessment tools provided by security vendors often emphasize weaknesses that their products address while minimizing areas where their solutions provide limited value
- Generic Recommendations: Free tools frequently provide standardized advice that doesn't account for specific business contexts, industry requirements, or resource constraints
- Insufficient Context: Basic assessment tools often fail to explain why particular recommendations matter for business protection
The Valydex Approach to Privacy-First Assessment
Privacy-First Assessment Philosophy
iFeelTech's Cyber Assess Valydex represents a different approach to cybersecurity assessment, built on principles of privacy protection, educational value, and transparent guidance. Rather than collecting business data for marketing purposes, Valydex performs all assessments locally in the user's browser, ensuring that sensitive business information never leaves the organization's control.
This privacy-first design reflects the understanding that cybersecurity assessment tools should demonstrate security principles rather than create additional data exposure risks. By processing assessments locally, Valydex eliminates concerns about data sharing with unknown third parties while providing comprehensive security evaluations.
Comprehensive Framework Implementation
Valydex assessments evaluate all six NIST CSF 2.0 functions through targeted questions that reveal security gaps and implementation opportunities. The framework-based approach ensures comprehensive coverage rather than focusing on specific vendor solutions or limited security areas.
| Assessment Area | Key Evaluation Points | Business Impact |
|---|---|---|
| Governance | Leadership engagement, policy development, and risk management integration | Security alignment with business objectives |
| Asset Management | Inventory processes, data classification, and personnel security awareness | Visibility into technology footprint |
| Protection Controls | Access management, data security, employee training, technical safeguards | Prevention of security incidents |
| Detection | Monitoring systems, threat awareness, and incident identification | Early warning of security issues |
| Response Planning | Incident response procedures, communication protocols, and recovery planning | Minimized incident impact |
| Recovery | Backup systems, business continuity, and improvement processes | Rapid operation restoration |
Assessment Implementation and Results Interpretation
Preparation for Effective Assessment
Information Gathering
Before beginning any cybersecurity assessment, compile basic information about current technology usage, security tools, and business processes. This includes an inventory of devices, software applications, cloud services, and data handling procedures.
Stakeholder Involvement
Include relevant team members in assessment completion, particularly those responsible for IT management, administrative procedures, and customer data handling. Multiple perspectives often reveal security gaps that single-person assessments miss.
Time Allocation
Plan adequate time for thorough assessment completion rather than rushing through evaluation questions. Quality assessments typically require 30-60 minutes, depending on business complexity and current security maturity.
Understanding Assessment Results
Risk Scoring Interpretation: Assessment scores provide relative indicators of security maturity rather than absolute security guarantees. A high score indicates strong alignment with framework requirements, while lower scores identify improvement opportunities.
Priority Recommendations: Quality assessments prioritize recommendations based on risk reduction potential, implementation difficulty, and cost-effectiveness. To build security momentum before tackling complex projects, address high-priority, low-complexity improvements first.
For businesses ready to implement systematic security improvements, our quick cybersecurity wins guide provides actionable steps that can be completed immediately.
Common Implementation Challenges
- Resource Allocation: Small businesses often underestimate the time and effort required for security improvement implementation
- Technical Complexity: Some security recommendations require technical expertise that exceeds internal capabilities
- Change Management: Security improvements often require procedure changes that affect daily operations
- Cost Management: Security improvements involve both direct costs for tools and services, plus indirect costs for implementation time
Professional Consultation and Advanced Assessment
When to Seek a Professional Security Assessment
Compliance Requirements
Organizations subject to regulatory requirements like HIPAA, PCI DSS, or SOC 2 typically need professional security assessments to demonstrate compliance adequacy. Self-assessment tools provide preparation but rarely satisfy regulatory documentation requirements.
Complex Technology Environments
Businesses with multiple locations, cloud services, or integrated systems often require professional assessment to evaluate security across complex technology architectures. Professional consultants provide technical expertise for comprehensive security evaluation.
Growth Planning
Rapidly growing businesses often outgrow basic security approaches and require professional guidance for enterprise-grade security implementation. Professional assessment helps plan security evolution that supports business growth rather than constraining it.
Professional Assessment Investment Planning
Based on 2025 market analysis, professional cybersecurity assessments typically follow these investment ranges:
| Business Size | Assessment Cost Range | Typical Scope |
|---|---|---|
| Under 50 Employees | $5,000-$15,000 | Comprehensive evaluation with basic testing |
| 50-250 Employees | $15,000-$35,000 | Advanced testing and compliance evaluation |
| 250+ Employees | $35,000-$50,000+ | Enterprise-level assessment with specialized testing |
Industry-Specific Assessment Considerations
Healthcare and Professional Services
Healthcare organizations and professional service firms face unique cybersecurity requirements due to client confidentiality obligations and regulatory compliance mandates. Standard cybersecurity assessments may not address industry-specific requirements like HIPAA compliance or attorney-client privilege protection.
Financial Services and E-commerce
Organizations handling financial data or processing payments require a specialized security assessment that addresses payment card industry (PCI DSS) requirements and financial data protection standards. These assessments typically include additional evaluation of transaction security, data encryption, and fraud prevention measures.
Manufacturing and Technology Companies
Organizations with intellectual property concerns or industrial control systems require specialized assessments that address information security and operational technology protection. These assessments often include evaluation of network segmentation, access controls, and physical security measures.
Comprehensive Security Implementation
Free cybersecurity assessment tools provide an essential starting point for security improvement, but comprehensive protection requires systematic implementation of identified recommendations. Organizations looking to implement advanced security measures can benefit from our cybersecurity software guide, which covers enterprise-grade tools suitable for growing businesses.
Critical Security Controls Implementation
Password Management
Password security remains among small businesses' highest-impact, lowest-cost security improvements. Our comprehensive password security guide provides detailed implementation strategies for improving authentication across your organization.
Backup and Recovery Systems
Regular, tested data backups provide essential protection against ransomware and system failures. Our business backup solutions guide covers both local and cloud-based protection options for businesses needing comprehensive backup strategies.
Security Monitoring and Response
Small businesses often lack the resources for 24/7 security monitoring, but basic monitoring capabilities can significantly improve threat detection. Organizations requiring ongoing security support should consider our managed IT services, which include continuous security monitoring and incident response.
Building Long-term Security Culture
Effective cybersecurity extends beyond technical controls to encompass organizational culture and ongoing education. Assessment results provide the foundation for building security awareness throughout your organization, but sustained improvement requires a systematic approach to security culture development.
For organizations conducting mid-year security audits, assessment results help track progress against established security goals and identify areas requiring additional attention.
Alternative Assessment Tools and Comparison
While Valydex provides comprehensive privacy-first assessment capabilities, businesses may benefit from understanding the broader assessment landscape. Our existing cybersecurity assessment tool comparison covers additional options, including CyberAssess, which offers complementary evaluation approaches for different business needs.
Assessment Tool Selection Criteria
When evaluating cybersecurity assessment tools, consider these critical factors:
- Privacy Protection: How the tool handles your business data during and after assessment
- Framework Alignment: Whether recommendations align with established standards like NIST CSF 2.0
- Implementation Guidance: Quality and specificity of improvement recommendations
- Business Context: Whether the tool considers your specific industry and business size
- Ongoing Support: Educational resources and implementation guidance provided
Frequently Asked Questions
How often should small businesses conduct cybersecurity assessments?
We recommend annual assessments as a baseline, with additional evaluations following significant technology changes, security incidents, or business growth. Regular assessments help ensure that security measures evolve with your business.
Can free assessment tools replace professional security consultation?
Free assessment tools provide excellent preparation and baseline evaluation, but complex environments or compliance requirements typically benefit from professional consultation. Use free tools to establish foundations, then seek professional guidance for advanced implementation.
What should I do if my assessment reveals significant security gaps?
First, prioritize high-impact, low-complexity improvements. Focus on basic security hygiene, such as password management and software updates, before pursuing advanced security measures. Consider professional consultation for complex technical implementations.
How do assessment results help with cybersecurity budgeting?
Assessment results provide concrete justification for security investments by identifying specific risks and quantifying potential impact. Use results to prioritize spending and demonstrate ROI for security improvements to stakeholders.
Are privacy-first assessment tools as effective as traditional options?
Privacy-first tools like Valydex can be more effective because they eliminate data sharing concerns that often prevent honest assessment completion. Local processing ensures complete privacy while providing comprehensive evaluation capabilities.
How do cybersecurity assessments support compliance requirements?
While assessments based on frameworks like NIST CSF 2.0 provide excellent preparation for compliance audits, they typically don't replace formal compliance evaluation. Use assessment results to identify gaps before official compliance reviews.
What's the difference between security assessment and penetration testing?
Security assessments evaluate overall security posture through questionnaires and policy review, while penetration testing involves technical attacks against systems to identify vulnerabilities. Most small businesses benefit from assessment before considering penetration testing.
Conclusion
Free cybersecurity assessment tools have evolved into valuable business resources that provide actionable security guidance without requiring significant upfront investment. The most effective options combine comprehensive framework alignment with privacy protection and educational support, enabling systematic security improvement.
Quality assessment tools like Valydex demonstrate that practical cybersecurity evaluation can respect business privacy while providing professional-grade insights into security posture and improvement opportunities. By aligning with established frameworks like NIST CSF 2.0, these tools offer guidance that reflects industry best practices rather than vendor-specific solutions.
The key to successful cybersecurity assessment lies in selecting tools that provide honest evaluation, actionable recommendations, and ongoing educational support. Assessment should be the foundation for systematic security improvement rather than a one-time compliance exercise.
For small businesses beginning their cybersecurity journey, free assessment tools are essential for building security awareness and identifying immediate improvement opportunities. As businesses grow and security requirements become more complex, professional consultation can build upon the foundation established through systematic self-assessment.
Organizations seeking comprehensive security improvement should consider our complete range of resources, from basic business software recommendations to advanced enterprise security solutions designed to support systematic security enhancement.
For comprehensive implementation guidance and ongoing security education, explore the complete Valydex resource library, which includes step-by-step implementation guides, tool comparisons, and industry-specific security frameworks.