Published: August 27, 2025 | Last updated: August 27, 2025
Key Takeaway: DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an email security standard that prevents cybercriminals from sending fraudulent emails using your business domain. According to the FBI's latest available data, email-based fraud represented a significant portion of the $12.5 billion in reported cybercrime losses in 2023. Implementing DMARC protection has become an important security measure for businesses of all sizes.
Email remains a primary communication channel for businesses, making it an attractive target for cybercriminals. While most business owners understand the importance of comprehensive cybersecurity measures, email authentication often receives less attention despite being an effective defense against fraud schemes.
The landscape has evolved with major email providers implementing authentication requirements. Google and Yahoo introduced DMARC requirements for bulk senders in February 2024, while Microsoft began enforcing similar requirements for Outlook.com users on May 5, 2025. These changes make email authentication both a security measure and a deliverability requirement.
Understanding Email-Based Business Threats
The FBI's Internet Crime Complaint Center (IC3) consistently reports billions in losses from email-based cybercrime schemes. Business Email Compromise (BEC) attacks represent a significant portion of these incidents, typically involving cybercriminals impersonating company executives, vendors, or trusted partners to trick employees into transferring money or sensitive information.
Small businesses face particular challenges because they often manage email security alongside numerous other responsibilities while maintaining valuable business relationships that criminals attempt to exploit.
Common Email-Based Attack Scenarios:
- Executive Impersonation: Emails appearing to come from leadership requesting urgent wire transfers
- Vendor Fraud: Criminals impersonating suppliers requesting payment to different accounts
- Payroll Diversion: Fraudsters posing as employees requesting payroll redirections
- Customer Deception: Criminals sending invoices using your company's domain
What is DMARC? A Clear Explanation
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It functions as a verification system that helps email providers determine whether messages claiming to come from your business domain are legitimate.
DMARC works alongside two other email authentication protocols to create comprehensive protection:
SPF (Sender Policy Framework)
SPF specifies which mail servers are authorized to send email from your domain. Think of it as maintaining an approved sender list that email providers can verify against.
DKIM (DomainKeys Identified Mail)
DKIM adds a digital signature to outgoing emails, proving they originated from your domain and haven't been altered during transmission.
DMARC Integration
DMARC ties SPF and DKIM together and instructs email providers what to do when emails fail authentication checks. It also provides detailed reports about all emails sent from your domain.
Email Authentication Process:
- Someone sends an email claiming to be from your business domain
- The receiving email provider checks your SPF record to verify the sending server
- The provider validates the DKIM signature to confirm message authenticity
- DMARC checks if the email meets alignment requirements
- Based on your DMARC policy, the email is delivered, quarantined, or rejected
- You receive detailed reports about authentication attempts
Business Benefits of DMARC Implementation
Enhanced Email Security
DMARC implementation helps prevent cybercriminals from successfully impersonating your business in email attacks. DMARC can significantly reduce domain spoofing attempts when properly configured with an enforcement policy.
For example, if a criminal attempts to send an email to one of your customers requesting payment to a fraudulent account, DMARC enforcement would help email providers identify the fraudulent message and handle it according to your specified policy.
Improved Email Deliverability
DMARC implementation often improves email deliverability for legitimate business communications. Email providers view authenticated domains as more trustworthy, which can result in better inbox placement for your marketing emails, customer communications, and automated notifications.
Major email providers now consider authentication status when making delivery decisions, making DMARC implementation valuable for reliable email delivery.
Compliance with Current Requirements
Email provider requirements have evolved significantly:
Google and Yahoo Requirements (February 2024):
- SPF, DKIM, and DMARC are required for senders of 5,000+ daily emails
- Spam complaint rates must remain below 0.3%
- One-click unsubscribe required for marketing emails
Microsoft Outlook.com Requirements (May 5, 2025):
- DMARC authentication is required for bulk senders
- Non-compliant emails may receive SMTP rejection
- Enhanced monitoring through feedback mechanisms
Brand Protection and Monitoring
DMARC provides visibility into all emails your domain sends, including unauthorized usage attempts. This monitoring capability helps protect your brand reputation by providing insights into potential impersonation attempts.
The reporting component also offers valuable insights into your email infrastructure, helping identify legitimate sending sources that may need proper authentication configuration.
DMARC Implementation Phases
DMARC implementation typically follows a three-phase approach that balances security with operational requirements:
Phase 1: Monitoring (p=none)
The initial DMARC policy uses p=none, which provides comprehensive reporting without affecting email delivery. This monitoring phase serves several purposes:
- Infrastructure Discovery: Identify all legitimate sources sending email from your domain
- Authentication Assessment: Evaluate current SPF and DKIM configuration
- Threat Intelligence: Monitor attempted spoofing attacks
- Operational Safety: Ensure legitimate email continues flowing normally
Most businesses remain in monitoring mode for 30-90 days while analyzing reports and addressing authentication issues.
Phase 2: Quarantine (p=quarantine)
After resolving authentication issues, businesses typically implement a quarantine policy. This configuration instructs email providers to treat authentication failures as suspicious, typically routing such messages to spam folders rather than primary inboxes.
Quarantine policies protect while maintaining some email delivery for cases that might not authenticate properly due to forwarding or other complications.
Phase 3: Enforcement (p=reject)
The strongest DMARC protection uses a reject policy instructs email providers to block emails that fail authentication checks. This configuration provides maximum protection but requires careful implementation to avoid blocking legitimate email.
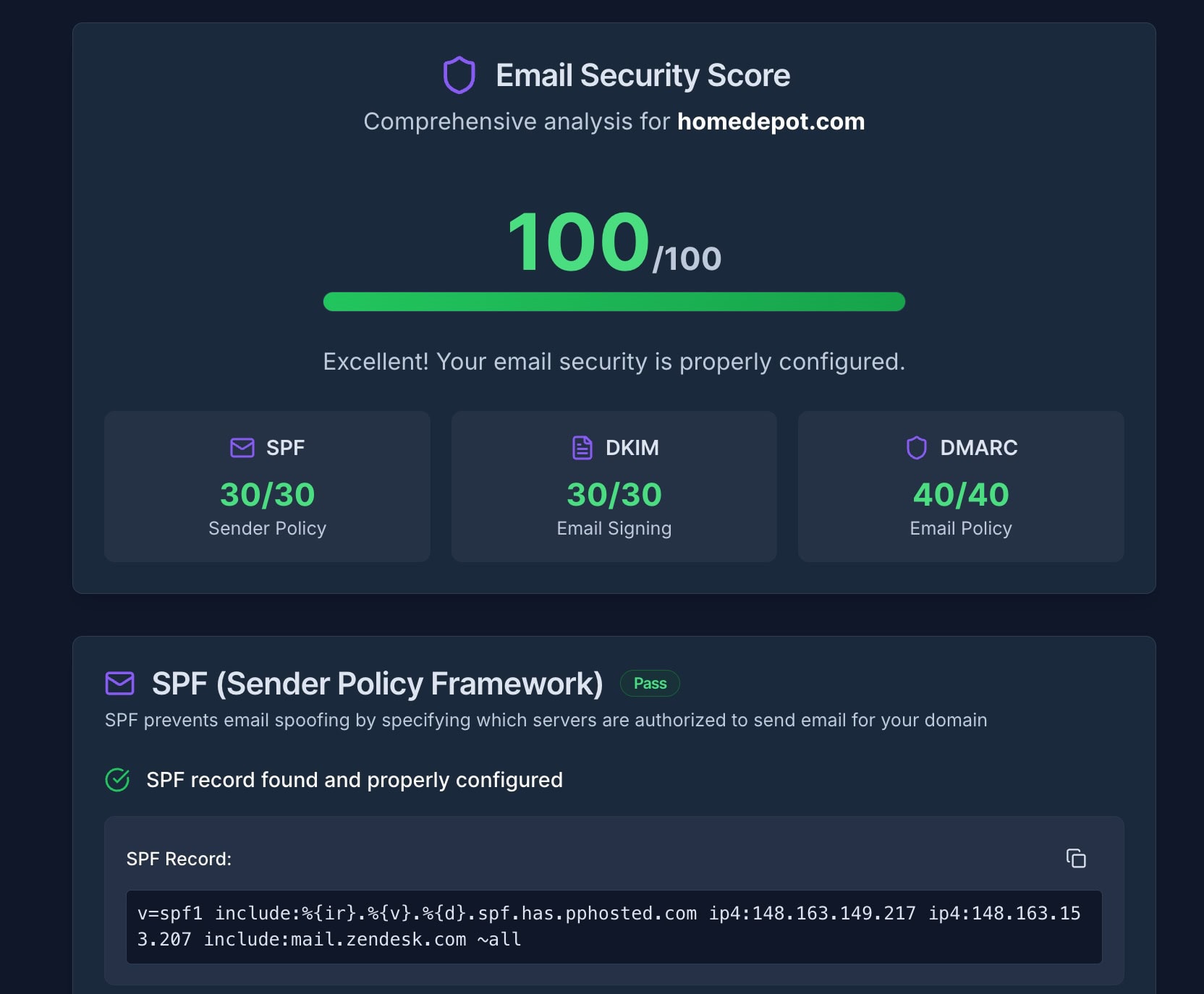
valydex.com email security checker result
DMARC Capabilities and Limitations
What DMARC Protects Against
- Domain spoofing attacks using your exact business domain
- Executive impersonation emails appearing to come from company leadership
- Vendor fraud attempts using your domain to deceive customers
- Automated spoofing campaigns targeting your domain
Additional DMARC Benefits
- Detailed reporting on email authentication attempts
- Improved deliverability for legitimate business email
- Compliance with email provider requirements
- Enhanced visibility into email infrastructure usage
DMARC Limitations
DMARC cannot prevent all email-based attacks:
- Look-alike Domain Attacks: Criminals using domains similar to yours
- Display Name Spoofing: Attacks using your business name but different email addresses
- Account Compromise: Legitimate email accounts that have been compromised
- Social Engineering: Attacks that don't rely on technical impersonation
Important Considerations
- DMARC requires ongoing monitoring and maintenance
- Implementation complexity increases with email infrastructure complexity
- Forwarding and mailing lists can cause legitimate email to fail authentication
- Complete email security requires addressing multiple attack vectors
Getting Started: DMARC Implementation Steps
Step 1: Assess Current Email Authentication
Before implementing DMARC, evaluate your existing SPF and DKIM configuration. During this assessment, many businesses discover authentication gaps that need to be resolved before DMARC deployment.
A quick way to check your current email security status is to use an automated testing tool to identify potential authentication issues and provide immediate feedback on your domain's configuration.
Step 2: Configure SPF and DKIM
Proper DMARC implementation requires functional SPF and DKIM authentication:
SPF Configuration:
- Identify all legitimate email sending sources for your domain
- Create SPF records that authorize these sources
- Address the 10 DNS lookup limit through record optimization
DKIM Setup:
- Configure DKIM signing for your primary email platform
- Set up proper key rotation schedules
- Ensure DKIM alignment with your domain
Step 3: Publish Initial DMARC Record
Start with a monitoring policy to gather intelligence without affecting email delivery:
This record configuration sets the policy to monitor only (p=none), requests aggregate reports (rua=), requests failure reports (ruf=), and generates reports for all authentication failures (fo=1).
Step 4: Monitor and Analyze Reports
DMARC generates two types of reports:
- Aggregate Reports: Daily summaries showing authentication results for all emails sent from your domain
- Failure Reports: Real-time notifications about specific authentication failures
Analyzing these reports helps identify legitimate email sources that need authentication fixes and provides visibility into potential spoofing attempts.
Step 5: Progress to Enforcement
After resolving authentication issues identified through monitoring, gradually implement enforcement policies:
- Test Quarantine: Implement
p=quarantinefor a percentage of emails using thepct=tag - Full Quarantine: Apply quarantine policy to all emails after testing
- Test Rejection: Implement
p=rejectfor a percentage of email - Full Enforcement: Apply the reject policy to all emails for maximum protection
Industry-Specific Implementation Considerations
Professional Services
Law firms, accounting practices, and consulting businesses should prioritize DMARC implementation due to their access to sensitive client information and trust relationships. Implementation should focus on strong enforcement policies while carefully managing authentication for client communication systems.
Healthcare Practices
Healthcare organizations must balance email security with reliable communication for patient care. DMARC implementation should account for various medical systems that may send patient communications and ensure authentication doesn't interfere with healthcare workflows.
E-commerce Businesses
Online retailers benefit significantly from DMARC implementation due to high email volumes for order confirmations, shipping notifications, and marketing communications. Strong authentication improves deliverability while protecting customers from fraudulent communications.
Financial Services
Banks, credit unions, and financial advisors represent high-value targets for email-based attacks. DMARC enforcement policies provide important protection against impersonation attacks while supporting compliance requirements for financial communications.
DMARC Management Tools and Platforms
While basic DMARC can be implemented manually, most businesses benefit from specialized platforms that simplify management and provide actionable insights from report analysis.
Key Platform Features to Consider:
- Report Processing: Automated parsing and analysis of DMARC reports
- Policy Management: Tools for safe policy transitions from monitoring to enforcement
- Threat Intelligence: Identification and analysis of spoofing attempts
- Integration Support: Compatibility with existing email infrastructure
- MSP Features: Multi-tenant management for service providers
EasyDMARC
Comprehensive platform featuring automated report analysis, EasySPF record flattening, and MTA-STS/TLS-RPT support. EasyDMARC includes an MSP program for service providers managing multiple client domains.
DMARCReport
This product focuses on white-label capabilities for MSPs with volume-based pricing tiers. It includes MTA-STS and TLS-RPT tooling alongside standard DMARC features.
dmarcian
Enterprise-focused platform with detailed forensic analysis and policy optimization recommendations. Strong reporting capabilities for complex email infrastructures.
Implementation Investment Analysis
Implementation Costs
Direct Costs:
- DMARC platform subscription: $25-$300+ monthly, depending on email volume
- Professional implementation services: $2,000-$8,000 for complex environments
- Staff time for monitoring and policy management: 2-8 hours monthly
Indirect Considerations:
- Potential temporary email deliverability adjustments during implementation
- Time investment in report analysis and policy optimization
- Training for staff responsible for email security management
Business Value
Direct Benefits:
- Protection against email-based fraud attempts
- Reduced customer support costs from impersonation-related issues
- Improved marketing email deliverability and engagement rates
Risk Management Value:
- Protection of business relationships through reduced spoofing success
- Enhanced business reputation through demonstrated security commitment
- Compliance with email provider authentication requirements
Common Implementation Challenges and Solutions
Challenge 1: Complex Email Infrastructure
Issue: Businesses using multiple email platforms, marketing tools, and automated systems often face comprehensive authentication setup challenges.
Solution: During the monitoring phase, conduct a thorough inventory of all email sending sources. Use DMARC reports to identify previously unknown sending sources and configure appropriate authentication.
Challenge 2: Third-Party Service Integration
Issue: Many business tools send emails on behalf of your domain without proper authentication configuration.
Solution: Work with third-party service providers to configure SPF authorization and DKIM signing. To simplify authentication management, consider using dedicated subdomains for third-party services.
Challenge 3: Email Forwarding Complications
Issue: Legitimate email forwarded through personal accounts or distribution lists may fail DMARC authentication.
Solution: Implement ARC (Authenticated Received Chain) where possible, use relaxed alignment policies, or educate users about forwarding limitations. Consider alternative communication methods for frequently forwarded content.
Challenge 4: False Positive Management
Issue: Legitimate email occasionally fails authentication due to infrastructure issues or edge cases.
Solution: Maintain monitoring alongside enforcement policies to identify authentication failures. Implement gradual policy deployment using percentage-based enforcement to minimize impact while maintaining protection.
Measuring DMARC Implementation Success
Key Performance Indicators
Security Metrics:
- Percentage of email passing DMARC authentication
- Number of identified spoofing attempts per month
- Reduction in customer-reported impersonation incidents
- Time to detect and respond to new spoofing campaigns
Operational Metrics:
- Email deliverability rates for legitimate communications
- Marketing email engagement rates and complaint levels
- Customer support tickets related to email authentication
- Staff time required for DMARC management and monitoring
Regular Assessment Schedule
Weekly Reviews: Authentication failure trends, new legitimate sending sources, spoofing attempt patterns
Monthly Assessments: Overall authentication success rates, policy enforcement impact on deliverability, cost-benefit analysis updates
Quarterly Evaluations: Strategic review of DMARC policy effectiveness, new email infrastructure requirements, and evaluation of additional security enhancements
Pro Tip: Integration with Broader Security Strategy
DMARC works best as part of a comprehensive cybersecurity strategy. For maximum protection, consider combining DMARC implementation with employee security awareness training, multi-factor authentication, and regular security assessments.
For additional cybersecurity guidance and educational resources, explore comprehensive security resources covering various aspects of business email protection and threat prevention.
Frequently Asked Questions
How long does DMARC implementation typically take?
Although initial DMARC record publication can be completed in one day, proper implementation usually takes 3-6 months to progress from monitoring to full enforcement. This timeline allows for thorough testing and resolving authentication issues with legitimate email sources.
Will DMARC interfere with legitimate business email?
When properly implemented, DMARC should not interfere with legitimate email. The monitoring phase identifies potential issues before enforcement begins, and gradual policy deployment minimizes the risk of false positives. However, some forwarded emails and misconfigured third-party services may require attention.
Is DMARC implementation required for all businesses?
While not universally required by law, DMARC is now necessary for businesses sending more than 5,000 emails daily to Gmail or Yahoo addresses. Microsoft's May 2025 enforcement also affects bulk senders to Outlook.com addresses. Beyond compliance, DMARC provides valuable fraud protection for businesses of all sizes.
Can businesses implement DMARC without technical expertise?
Basic DMARC monitoring can be implemented with minimal technical knowledge, but proper deployment typically requires DNS management skills and understanding of email infrastructure. Many businesses benefit from professional implementation services or managed platforms that simplify the process.
What happens to an email that fails DMARC authentication?
The action depends on your DMARC policy setting. With p=none (monitoring), failed emails are delivered normally while generating reports. With p=quarantine, failed emails typically go to spam folders. With p=reject, failed emails are blocked and not delivered to recipients.
What are typical DMARC implementation costs?
Creating DMARC records is free, but most businesses benefit from management platforms that cost $25-$300+ monthly, depending on email volume. Professional implementation services range from $2,000-$8,000 for complex environments. The investment typically provides good value by helping prevent fraud attempts.
How does DMARC work with email marketing platforms?
Email marketing platforms like Mailchimp, Constant Contact, and others typically provide DMARC authentication support. You'll need to configure SPF and DKIM records for these services and ensure they align with your DMARC policy. Most reputable platforms offer documentation for proper setup.
Next Steps: Implementing DMARC for Your Business
DMARC implementation represents an essential investment in email security for small and medium businesses. The combination of fraud prevention, deliverability improvement, and compliance benefits makes implementation valuable for most organizations using email for business communications.
Immediate Action Items:
- Assess Current State: Test your current email security configuration and evaluate existing SPF and DKIM setup to identify authentication gaps
- Start Monitoring: Implement a DMARC monitoring policy to gather intelligence about your email infrastructure
- Analyze Reports: Review DMARC reports to understand legitimate sending sources and potential security issues
- Plan Enforcement: Develop a timeline for progressing from monitoring to quarantine to reject policies
The email threat landscape continues evolving, with cybercriminals developing increasingly sophisticated email-based attacks. However, proper DMARC implementation protects against domain spoofing while supporting business communication requirements. Investing in email authentication helps prevent significantly larger costs from successful fraud attacks.
For businesses ready to enhance their email security posture, DMARC represents an essential foundation for comprehensive email protection. Combined with employee security training, additional security measures, and ongoing monitoring, DMARC implementation substantially reduces email-based fraud risk while supporting reliable business communication.
Disclosure: This article contains affiliate links to email security platforms. We may earn a commission when you sign up for services through our links at no additional cost to you. Our recommendations are based on professional experience and a thorough evaluation of platform capabilities.
This article is part of our comprehensive email security series. Next week, we'll cover the specific compliance requirements introduced by Gmail, Yahoo, and Microsoft in 2024-2025, including practical steps for meeting new bulk sender requirements and maintaining good sender reputation.
For personalized assistance with DMARC implementation or comprehensive email security planning, contact our cybersecurity team for a consultation tailored to your business needs.