Most business owners know they should care about cybersecurity, but many aren't sure how secure they actually are. It's a common scenario: you've set up some basic protections, maybe installed antivirus software, and told your team to use strong passwords. But beyond that? The picture gets fuzzy.
This uncertainty isn't unusual. Cybersecurity has traditionally been the domain of IT professionals speaking in technical terms about frameworks, compliance standards, and risk assessments. For the average business owner trying to run their company, it can feel like a foreign language.
Why Every Business Needs a Security Baseline
The numbers tell a clear story: small and medium businesses face the same cyber threats as large corporations, but often with fewer resources to defend themselves. According to recent studies, 43% of cyberattacks target small businesses, and many of these incidents could be prevented with basic security measures.
The challenge isn't necessarily knowing that security matters—it's understanding what “good enough” security looks like for your specific situation. A solo consultant doesn't need the same security infrastructure as a 200-person manufacturing company, but both need protection appropriate to their size and risk level.
Understanding the NIST Cybersecurity Framework 2.0
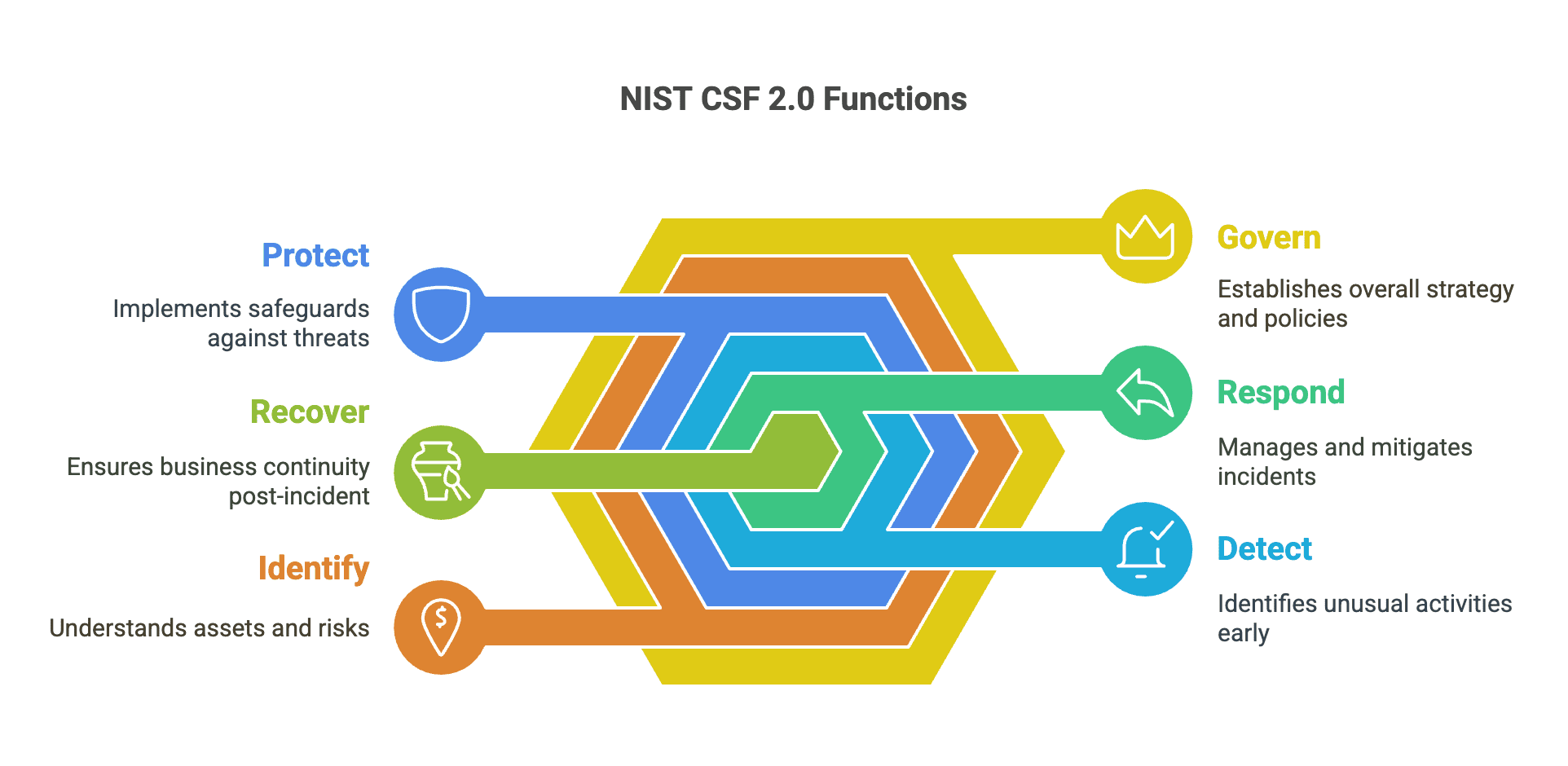
It helps to have a roadmap to understand cybersecurity. The National Institute of Standards and Technology (NIST) provides exactly that with its Cybersecurity Framework, a set of guidelines used by organizations worldwide to manage cybersecurity risk.
Think of NIST 2.0 as a structured way to think about security, organized around six core functions that any organization can understand and apply:
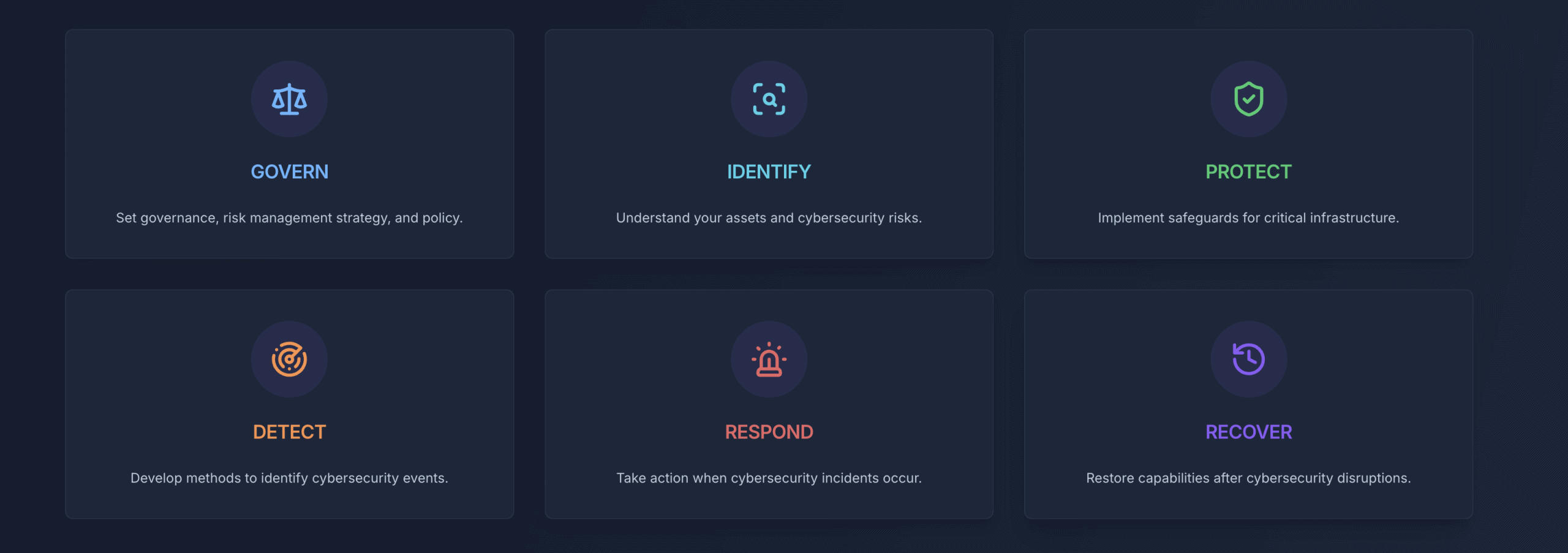
GOVERN: Setting the Foundation
This covers who's responsible for security decisions, what policies you have in place, and how security fits into your overall business planning. For a small business, this might be as simple as designating someone to handle security decisions and writing down basic rules about password use and software updates.
IDENTIFY: Know What You're Protecting
You can't secure what you don't know you have. This function involves understanding your business assets—computers, software, data, and systems—and recognizing which ones are most critical to your operations. It also means staying informed about potential threats to your industry.
PROTECT: Building Your Defenses
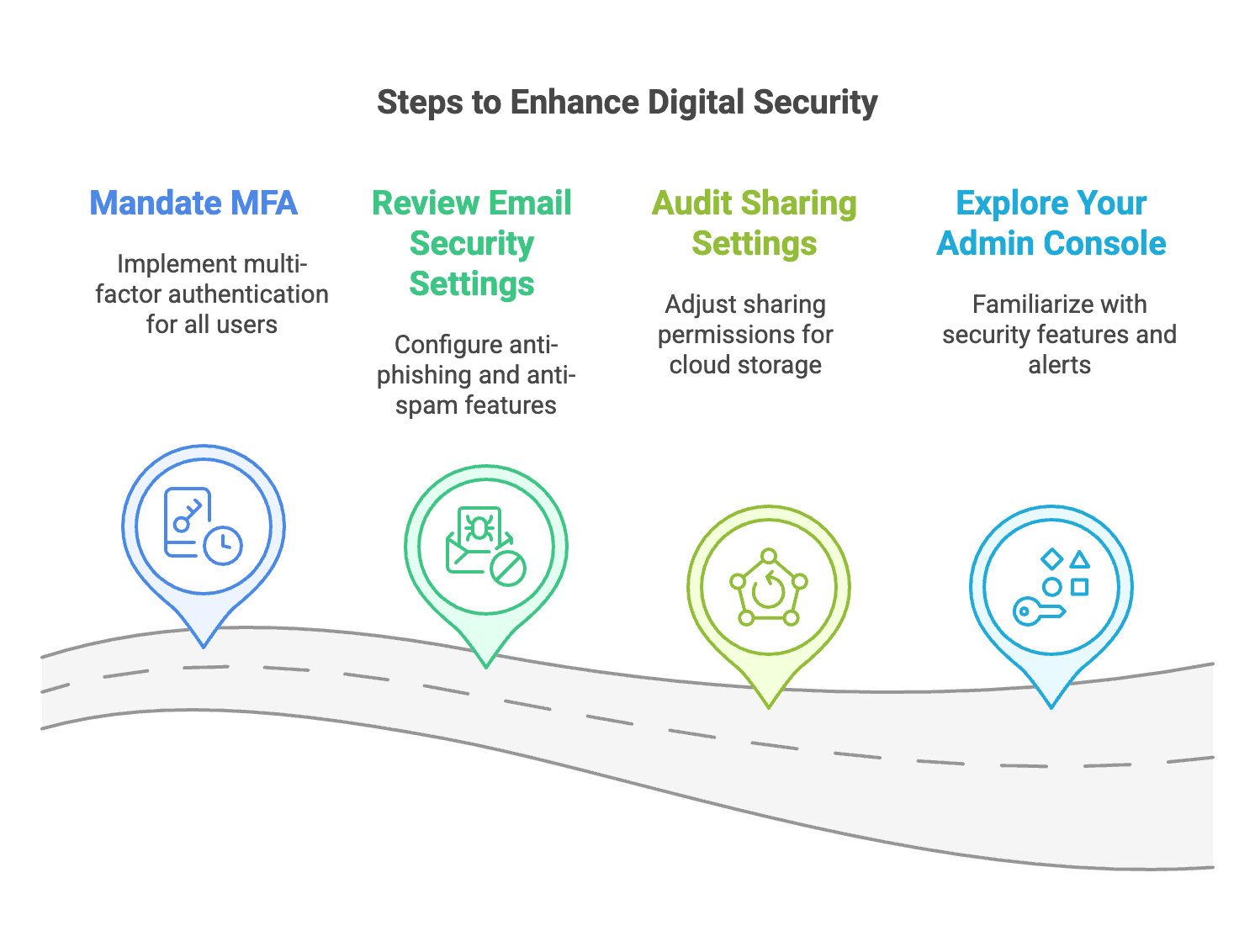
When they hear “cybersecurity,” most people think of the tools and practices that prevent bad things from happening. This includes everything from password managers and software updates to employee training and data backups.
DETECT: Staying Alert
Even with good protections, problems can still occur. This function focuses on having systems and processes to notice when something unusual happens, whether that's a failed login attempt, suspicious network activity, or unusual file changes.
RESPOND: When Things Go Wrong
This covers having a plan for what to do when you discover a security problem. For many small businesses, this starts with knowing who to call for help and having basic steps documented for common scenarios.
RECOVER: Getting Back to Business
This function addresses how to restore normal operations after an incident and what you can learn to prevent similar problems in the future. At its most basic level, this often centers around having good data backups and tested recovery procedures.
From Framework to Practice
While the NIST framework provides structure, translating it into actionable steps for your specific business can still feel overwhelming. This is where practical tools become valuable—they help bridge the gap between high-level concepts and day-to-day reality.
Understanding these security fundamentals becomes even more critical if you're setting up IT infrastructure for your business. Our comprehensive server room setup guide touches on many of these security considerations, but knowing your current baseline is the first step before implementing any new systems.
The “Where Do I Start?” Problem
The questions we hear most often from business owners reflect this translation challenge:
- “Are we doing enough to protect our business?”
- “What security gaps might we have that we don't even know about?”
- “How do we compare our size to other businesses?”
- “Where should we focus our limited time and budget first?”
These are smart questions, but finding clear, actionable answers has traditionally required expensive consultants or technical expertise that many smaller organizations simply don't have access to.
Enter Cyber Assess Valydex: Security Assessment Made Simple
That's exactly why we created Cyber Assess Valydex—a free, user-friendly cybersecurity self-assessment tool designed to give you that crucial bird's-eye view of your security posture in just minutes, not months.
Built around the NIST Cybersecurity Framework 2.0, Cyber Assess Valydex translates those six core functions into plain English questions that any business owner or team leader can understand and answer confidently. Instead of asking, “Do you have comprehensive identity and access management with automated provisioning?” We ask, “How do you handle passwords in your business?”
For businesses already implementing NIST CSF 2.0 cybersecurity tools, Cyber Assess Valydex provides an excellent way to validate your current implementation and identify any gaps in your security approach.
Three Assessments, One Goal: Clarity
Cyber Assess Valydex offers three assessment levels to meet you wherever you are in your cybersecurity journey:
Basic Assessment (5-10 minutes, 20 questions)
Perfect for small businesses and solopreneurs who want to understand fundamental security hygiene. Questions focus on the basics: password practices, software updates, data backups, and simple monitoring. No technical jargon—just straightforward questions about everyday security practices.
Standard Assessment (10-15 minutes, 45 questions)
This level is ideal for growing businesses with some IT resources that want to formalize their security practices and align with industry standards. It introduces concepts like documented policies, regular security reviews, and systematic approaches to common security challenges.
Comprehensive Assessment (15-25 minutes, 75 questions)
Designed for larger organizations that are ready to evaluate enterprise-level security programs and advanced controls. Questions cover sophisticated topics like threat intelligence, advanced monitoring, and formal governance structures.
More Than Just a Score: Your Security Roadmap
Unlike other security tools that leave you with just a number, Cyber Assess Valydex provides:
- NIST-aligned gap identification: Results organized around the six core functions, showing specific areas where your security could be stronger
- Prioritized recommendations: Focus on what matters most for your business size and type, with clear explanations of why each recommendation matters
- Budget-conscious suggestions: Solutions ranging from free tools to enterprise platforms, with realistic cost expectations
- Quick wins: High-impact actions you can implement immediately, often without spending money
- Professional baseline: Results you can confidently share with IT professionals or use as a starting point for security planning
Common Security Gaps and Quick Fixes
While every organization is different, certain security gaps appear frequently in assessments:
Password Problems
Many businesses still rely on simple passwords or password reuse. A password manager can solve this problem in an afternoon and dramatically improve security.
Missing Backups
Regular, tested data backups remain one of the most cost-effective security measures, yet many organizations discover their backup strategy has gaps only when they need it most.
Unmanaged Software Updates
Keeping software current closes known security vulnerabilities. Setting up automatic updates where possible can eliminate this gap with minimal ongoing effort.
Lack of Team Training
Employees often want to do the right thing, but aren't sure what that looks like. Simple, regular training on recognizing suspicious emails and following security policies can prevent many common incidents.
For small businesses building their IT foundation, our small business server setup guide addresses many of these fundamental security considerations in the context of establishing proper IT infrastructure.
Privacy First, Value Always
We believe in putting privacy first. Cyber Assess Valydex requires no signup, collects no personal data, and stores nothing on our servers. Take the assessment, get your results, and use them however best for your organization—no strings attached.
Starting the Conversation That Matters
Perhaps most importantly, Cyber Assess Valydex helps you start having cybersecurity conversations within your organization. This can involve bringing security topics to team meetings, justifying budget for security improvements, or simply getting everyone thinking about digital protection as part of daily operations.
The assessment results give you concrete talking points and a shared understanding of where you stand—invaluable for getting buy-in from leadership, staff, or external partners. Having NIST-aligned results also provides credibility when discussing security with IT professionals, insurance providers, or business partners.
Your Security Journey Starts Now
Cybersecurity doesn't have to be overwhelming or mysterious. With Cyber Assess Valydex, you can gain clarity about your current security posture and chart a path forward—all in the time it takes to grab a coffee.
Whether you use the results to guide your own improvements, share them with your IT team, or take them to a cybersecurity professional for deeper consultation, you'll have something concrete to build upon. The NIST framework provides the structure, and Cyber Assess Valydex makes it accessible.
Ready to see where you stand? Visit Cyber Assess Valydex and take your first step toward better cybersecurity. Understanding your security posture is the first step toward improving it.
Frequently Asked Questions About Cyber Assess Valydex
What is Cyber Assess Valydex, and how does it work?
Cyber Assess Valydex is a free cybersecurity self-assessment tool based on the NIST Cybersecurity Framework 2.0. It evaluates your organization's security posture through plain-English questions across six core functions: Govern, Identify, Protect, Detect, Respond, and Recover. The assessment takes 5–25 minutes depending on which tier you choose, and provides actionable recommendations based on your responses.
Do I need technical knowledge to complete the assessment?
No. Cyber Assess Valydex is specifically designed for non-technical users. We translate complex cybersecurity concepts into everyday business language. Questions ask about practical activities like “How do you handle passwords in your business?” rather than using technical jargon. Tooltips provide additional context when needed.
What is the difference between the three assessment tiers?
The Basic tier (20 questions, 5–10 minutes) focuses on fundamental security hygiene for small businesses. The Standard tier (45 questions, 10–15 minutes) is ideal for growing businesses wanting to formalize security practices. The Comprehensive tier (75 questions, 15–25 minutes) evaluates enterprise-level security programs with advanced controls.
Is my data collected or stored during the assessment?
No. Cyber Assess Valydex is completely privacy-first. We require no signup, collect no personal data, and store nothing on our servers. Your assessment is completed entirely in your browser, and you can save or share your results however you choose.
How accurate are the recommendations I receive?
Cyber Assess Valydex recommendations are based on industry-standard NIST guidelines and are tailored to your specific responses, business size, and identified gaps. While the tool provides excellent directional guidance, we always recommend consulting with cybersecurity professionals for detailed implementation planning, especially for larger organizations.
Can I retake the assessment to track improvement?
Absolutely. We encourage organizations to retake assessments periodically to track security improvements over time. Since we don't store data, you'll need to save your results locally if you want to compare scores, but this approach ensures your privacy while allowing you to measure progress.
What should I do with my assessment results?
Your results can be used in several ways: as a starting point for internal security planning, shared with IT professionals or consultants for deeper analysis, presented to leadership to justify security investments, or used to guide conversations with insurance providers or business partners about your security posture.
How often should I complete a cybersecurity assessment?
We recommend annual assessments as a baseline, with additional assessments when you make significant technology changes, experience security incidents, or undergo business transitions like growth, mergers, or new regulatory requirements. The assessment helps ensure your security measures keep pace with your business evolution.
Are the recommended tools and services affiliated with Cyber Assess Valydex?
Yes, some of our tool recommendations include affiliate partnerships, which we clearly disclose. These partnerships help us keep Cyber Assess Valydex completely free while recommending tools we genuinely use and trust. Our recommendations are based on assessment gaps and business needs, not commission potential.
Can Cyber Assess Valydex help with compliance requirements?
While Cyber Assess Valydex is built on the NIST framework used by many compliance standards, it's not a formal compliance audit tool. However, the assessment can help you understand your current posture relative to NIST guidelines and identify areas that may need attention for various compliance requirements. Always consult with compliance professionals for formal regulatory assessments.
—
Cyber Assess Valydex is entirely free and requires no signup. Start your assessment at valydex.com and discover your cybersecurity baseline in minutes.